AWS CloudTrail 101: How to Keep Tabs on Every Action in Your AWS Environment
.png)
Introduction
AWS CloudTrail is a logging service that tracks all user activity and API calls in your AWS environment. It provides an audit trail of actions taken by users, roles, or even AWS services, helping you answer critical questions like “Who made this change?” or “When was this resource created or deleted?” CloudTrail is essential for governance, compliance, and operational auditing of AWS accounts. In this article, we’ll explore CloudTrail’s features and capabilities, how it works (including log generation, storage, and querying), how it differs from Amazon CloudWatch, common use cases, and the latest CloudTrail pricing.
What Is AWS CloudTrail?

AWS CloudTrail is an AWS service that automatically records events in your account, including actions taken through the AWS Management Console, AWS CLI, SDKs, and other AWS services. These events capture details such as who performed the action, when it occurred, which API call was made, and which resources were affected. By providing this visibility into activity, CloudTrail enables:
- Security Auditing & Compliance: Full history of API calls to help meet auditing requirements for frameworks like SOC, PCI, and HIPAA.
- Change Tracking: Monitor changes to configurations and resources (for example, IAM policy updates or EC2 instance terminations) for troubleshooting and governance.
- Incident Investigation: Quickly determine the sequence of actions if a security incident or unauthorized change is suspected.
- Operational Insights: Although primarily an auditing tool, CloudTrail logs can be analyzed to answer operational questions and debug issues in your AWS environment.
CloudTrail is always on by default for your AWS account. It automatically logs management events (control plane actions) for the past 90 days, which you can view as Event History in the AWS console at no charge. This means even without any setup, you already have a 90-day audit log of management operations (like creating or deleting AWS resources) accessible on AWS.
Key CloudTrail Features and Capabilities
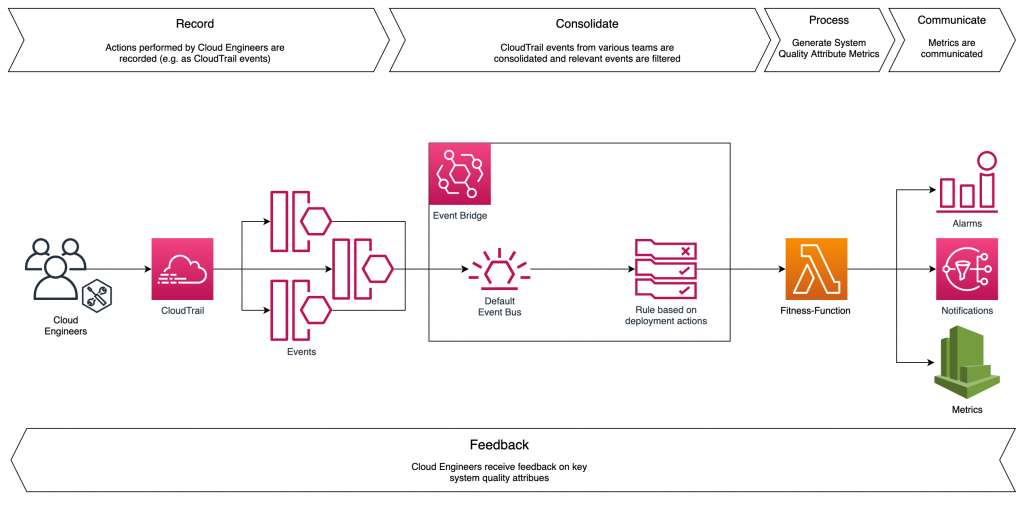
AWS CloudTrail offers several features that allow you to customize how you capture and analyze AWS activity logs:
- Event History: CloudTrail’s Event History provides a searchable record of the last 90 days of management events in each AWS Region. You can filter by attributes such as user, resource, service, or action and download these logs. This is enabled by default and free of charge for management events, giving you an immediate short-term audit log.
- Trails: To retain logs longer or track more types of events, you can create a Trail. A trail delivers a continuous stream of CloudTrail events to an Amazon S3 bucket for durable storage. You can configure trails to capture not only management events but also data events (resource-level API calls) and network activity events (VPC endpoint API traffic) as needed. Trails can be single-region or multi-region, and you can also set up an organization trail to consolidate events from all accounts in an AWS Organization. Optionally, CloudTrail trails can be configured to send logs to CloudWatch Logs for real-time monitoring and alerting, or to Amazon EventBridge to trigger workflows in response to certain actions.
- CloudTrail Lake: CloudTrail Lake is a managed data lake feature that lets you aggregate and analyze events directly within CloudTrail. It stores events in an optimized Apache ORC format for fast querying and allows you to run SQL-based or natural language queries on your audit logs without having to export them to another service. You can ingest events from AWS and external sources, then retain them for up to 7 or 10 years, depending on your chosen retention option. This feature is particularly useful for long-term retention and analysis of audit logs, whether for compliance or security investigations. Note: CloudTrail Lake usage—covering data ingestion, storage, and queries—is a paid feature.
- CloudTrail Insights: CloudTrail Insights is an optional feature that detects unusual activity in your AWS API usage. When enabled, CloudTrail analyzes management API calls to identify anomalies—such as a sudden spike in API calls or error rates—and automatically generates Insights events. These events alert you when something deviates from normal patterns—for example, if an API is called significantly more times than usual, which could indicate a script gone awry or a security issue. Insights events support proactive monitoring and are charged based on the number of events analyzed, as detailed in the pricing information.
- Event Categories – Management vs. Data vs. Network Events: CloudTrail categorizes events into different types:
- Management events (control plane operations) cover management actions on AWS resources (e.g., creating EC2 instances, updating IAM policies). These are logged by default.
- Data events (data plane operations) record high-volume resource-level actions, such as S3 object access or Lambda function invokes. These are not logged by default due to volume; you opt-in via trails for specific buckets, functions, etc.
- Network activity events capture API calls that traverse VPC Endpoints. Introduced in 2025, this feature logs both management and data API calls made via your VPC Interface Endpoints for deeper network-level visibility . Like data events, network events are opt-in.
- Insights events are generated by CloudTrail when it detects anomalies (as described above).
By selecting which event types to include in a trail through event selectors, you can control what CloudTrail records and optimize for both cost and relevance. For example, you might log all management events across your account but restrict data-event logging to only sensitive S3 buckets or critical Lambda functions.
- Multi-Account and Multi-Region Logging: CloudTrail can be enabled across multiple accounts via AWS Organizations. An organization trail ensures that every account in the org reports events to a central S3 bucket, simplifying company-wide auditing. Trails can also be created to apply to all regions, ensuring no activity in any region goes unnoticed.
- Integration with Other Services: CloudTrail works closely with AWS security and monitoring services. It can send events to Amazon CloudWatch Logs, which is useful for running CloudWatch Logs Insights queries or setting up metric filters and alarms on specific API calls. It also integrates with AWS EventBridge, letting you route specific events to automation workflows (for example, notifying the security team when IAM policies change). Many AWS services—such as AWS Config, AWS Security Hub, and GuardDuty—consume CloudTrail data to monitor compliance and detect threats. You can further analyze CloudTrail logs with services like Amazon Athena (by querying logs in S3) or with third-party SIEM tools.
How CloudTrail Works: Log Generation, Storage, and Querying

Understanding how CloudTrail captures and stores logs will help you use it effectively:
Event Generation: Whenever an action is taken in your AWS account – whether a user logs in, an API call is made via the CLI/SDK, or an AWS service performs an operation – CloudTrail records an event. Each event is a JSON record containing details like the event source (which AWS service), event name (which API call), timestamp, user identity, source IP, request parameters, and whether the action was successful. CloudTrail covers virtually all AWS services for management events, ensuring a comprehensive audit log. Data events (like S3 object access or Lambda executions) and network events (VPC endpoint traffic) are also recorded if you configure them in a trail. All events are typically available within minutes of the API call – CloudTrail delivers log files to S3 and internal event history usually within about 5 to 15 minutes of the recorded action, enabling near real-time auditing.
Storing Logs with Trails: To persist logs beyond 90 days or to log additional event types, you create a Trail. A trail defines where to deliver logs and which events to capture. When CloudTrail writes logs to an S3 bucket via a trail, it delivers periodic log files (compressed JSON.gz files) to your bucket. You can control the frequency of delivery (by default approx every 5 minutes if there are events). These S3 logs can be encrypted (using KMS) and have a predictable file structure. Many organizations set up a dedicated S3 bucket (often in a separate auditing account) to store CloudTrail logs from all accounts for long-term retention and analysis. Since the logs are in JSON, you can process them with AWS analytics tools like Amazon Athena (point Athena at the S3 bucket with CloudTrail logs and run SQL queries to find specific events) or ETL tools for further analysis. AWS even provides Athena query examples for CloudTrail logs. Additionally, if you enabled integration with CloudWatch Logs, each event is also sent to a CloudWatch Logs log group in near real-time, allowing you to search and filter events quickly or trigger CloudWatch Alarms (for example, alarm on any DeleteBucket API call in S3).
CloudTrail Lake for Querying: With CloudTrail Lake, AWS offers an integrated way to query CloudTrail logs without having to maintain S3 buckets and Athena tables yourself. When you create a CloudTrail Lake event data store, you choose which events to collect (you can ingest all events or filter by event type, AWS service, etc.). CloudTrail Lake will immutably store those events in a managed data store in the CloudTrail service . The data is stored in a highly optimized format (columnar ORC) for fast retrieval . You can then run SQL queries on this data right in the CloudTrail console (the query engine is backed by Athena). For example, you could query “all EC2 StartInstances events in the last 30 days” using SQL, or use the new natural language query feature to ask a question without knowing SQL . CloudTrail Lake also includes Lake dashboards for visualizing trends of events (e.g., which API is called most often) . Keep in mind that CloudTrail Lake is a paid feature – you pay for the data ingested, stored, and scanned by queries . The benefit is convenience and potentially faster performance for large datasets, as well as the ability to import historical CloudTrail logs from S3 (if you have older logs you want to bring into Lake for analysis).
Querying Logs Outside CloudTrail: If you are not using CloudTrail Lake, typical ways to query CloudTrail logs include:
- AWS Athena: As mentioned, you can define a schema for CloudTrail logs (AWS provides a CloudFormation template or Athena console wizard to do this) and query the log files directly from S3 with Athena. This is great for ad-hoc analysis without loading data into a database.
- CloudWatch Logs Insights: If you send CloudTrail to CloudWatch Logs, you can use CloudWatch Logs Insights, a query language for log data, to search and analyze the events. This is useful for more real-time searching (but note that long-term retention in CloudWatch Logs can become costly if not managed).
- Third-party tools: Many third-party log management or SIEM tools (Splunk, Elastic, Datadog, etc.) have integrations to ingest CloudTrail logs from S3 for centralized analysis and correlation with other data.
In summary, CloudTrail provides flexible options for log storage and querying: Event History for quick recent searches, Trails to S3 for long-term archival and external analysis, and CloudTrail Lake for integrated querying and long-term retention within AWS.
AWS CloudTrail vs. AWS CloudWatch
.png)
New AWS users often confuse CloudTrail with Amazon CloudWatch since both involve logging and monitoring. However, they serve different purposes. In short, CloudTrail records who did what on AWS, whereas CloudWatch monitors performance and health. CloudTrail is about auditing API activity, and CloudWatch is about metrics, operational monitoring, and alerting.

Despite these differences, CloudTrail and CloudWatch are complementary. For example, you might use CloudTrail to log an API call that changed a security group, and use CloudWatch to set an alarm that notifies you (via EventBridge rule) whenever such a CloudTrail event occurs. In practice, CloudTrail provides the audit log, and CloudWatch provides the monitoring and alerting mechanisms.
Common Use Cases for CloudTrail
AWS CloudTrail is useful in any scenario where tracking user actions and changes is important. Key use cases include:
- Security Auditing & Incident Response: CloudTrail is often the first place to turn during a security investigation. For example, if you suspect a compromised account or an unauthorized activity, you can search CloudTrail logs to see exactly what actions were taken and from which IP addresses. It’s invaluable for forensic analysis. Additionally, services like AWS GuardDuty consume CloudTrail events to detect threats (e.g. detecting if API calls are coming from unusual locations or by unusual principals). By keeping CloudTrail logs, you can answer “What happened in my account?” in detail .
- Compliance & Change Tracking: Many compliance standards require retaining audit logs of system activity. CloudTrail provides an immutable history of changes to your AWS environment, which can help in demonstrating compliance with regulations like PCI DSS, HIPAA, SOC 2, etc. For instance, CloudTrail logs can show that only authorized changes were made to critical resources, or produce a report of all access to sensitive data. AWS mentions using CloudTrail to prove compliance with various regulations as a key benefit . You can also use AWS Config alongside CloudTrail – AWS Config tracks state changes in resources, and CloudTrail logs the API calls that caused those changes, providing a full picture of what changed, when, and by whom.
- Operational Troubleshooting: When something goes wrong (a resource stops working, or was inadvertently modified), CloudTrail helps pinpoint the cause. Perhaps an IAM policy was changed and now a user gets AccessDenied errors – CloudTrail would show who changed the policy and what was changed. Or maybe an EC2 instance was terminated unexpectedly – CloudTrail would show the API call that terminated it and the user or service that called it. This level of detail is crucial for root cause analysis in a cloud environment where many actions are happening via automation.
- Resource Change Notifications: By integrating CloudTrail with EventBridge or CloudWatch, you can build automated responses or alerts for certain events. For example, you could have CloudTrail feed into an EventBridge rule so that any time an IAM role or policy is modified, a security team is notified or an approval workflow is triggered. Similarly, you might set up alarms for specific high-risk API calls (like deleting encryption keys, changing VPC security group rules, etc.). This turns CloudTrail from a passive log into an active monitoring tool, using AWS’s event-driven capabilities.
- Analytics and Insights on Usage: Over time, analyzing CloudTrail logs can reveal usage patterns. You might identify which APIs are most used (perhaps indicating areas to optimize or potential cost impacts), or detect an application’s behavior in terms of AWS service calls. CloudTrail Lake’s querying and dashboards can help surface these insights by summarizing API activity trends . This can benefit DevOps teams in understanding how different services are being used and optimize configurations or even costs.
For cloud beginners, it’s enough to remember that CloudTrail keeps a diary of everything that happens in your AWS account, which is indispensable for security and troubleshooting. For experienced DevOps and cloud engineers, CloudTrail becomes a fundamental component of audit logging strategy, often integrated with monitoring and security pipelines.
AWS CloudTrail Pricing
AWS CloudTrail pricing has several components, and it’s important to understand which CloudTrail features are free and which incur costs. Below is a breakdown based on the official CloudTrail pricing page (prices are as of 2025):
- Event History (Default 90-day Logs): Free.
- There is no charge for viewing and searching the past 90 days of management events via CloudTrail’s event history. This is included for all AWS accounts by default.
- Trail Delivery to S3 (Management Events): Free for one trail copy of management events.
- You can configure one trail to deliver a copy of all ongoing management events to an S3 bucket at no CloudTrail cost . This means CloudTrail doesn’t charge for the act of logging management events to S3 (consider it included in the service), but you will pay for the S3 storage of those logs (per S3’s pricing) and any access (GET/LIST) requests on the bucket. If you create additional trails that also capture the same management events (for example, multiple trails in different accounts or extra copies), those extra copies are billed. After the first free copy, management events delivered to S3 cost $2.00 per 100,000 events.
- Data Events and Network Events (Trail Logging):
- These are charged because they can be high-volume. Data events (such as S3 object-level logs, Lambda invoke logs) cost $0.10 per 100,000 events delivered to S3 . Similarly, the new Network activity events (VPC endpoint API calls) cost $0.10 per 100,000 events delivered to S3 . You are only charged for data or network events if you choose to enable them on a trail. (Management events remain free for one copy, as above.)
- CloudTrail Insights:
- If you enable CloudTrail Insights on a trail (to detect anomalies in API usage), it incurs a charge of $0.35 per 100,000 management events analyzed for each insight type . CloudTrail currently offers two Insights types – one for API call rate anomalies and one for error rate anomalies. Charges apply for each enabled type analyzing your events. This is in addition to the normal event logging costs.
- CloudTrail Lake – Ingestion and Storage: CloudTrail Lake has a separate pricing model based on data volume:
- Ingestion:
- Ingesting events into CloudTrail Lake costs $0.75 per GB for CloudTrail native events (management, data, and network events) . If you ingest other data sources into CloudTrail Lake (CloudTrail Lake can ingest from non-AWS sources or AWS services like AWS Config or Audit Manager), those are slightly cheaper at $0.50 per GB . Note: These costs are based on the uncompressed data size at ingestion time . For new CloudTrail Lake users, there is a free trial allowing up to 5 GB of ingestion in the first 30 days.
- Retention: CloudTrail Lake offers two retention options when you create an event data store – One-year extendable retention or Seven-year fixed retention.
- With the One-year (extendable) option, the first year of data retention is included in the ingestion cost . If you want to keep data beyond one year, you pay $0.023 per GB per month for extended retention , and you can extend retention up to 10 years maximum . This option is recommended if your volumes are relatively low (under ~25 TB per month).
- With the Seven-year retention option, you pay more upfront for ingestion, but that price includes up to 7 years of retention with no extra storage fees (you cannot extend beyond 7 years). The ingestion for this option uses tiered pricing: $2.50 per GB for the first 5 TB each month, $1.00 per GB for the next 20 TB, and $0.50 per GB beyond 25 TB in a month . This tiered model is cost-effective for large volumes of events and is recommended if you ingest over 25 TB of events per month.
- In summary, you choose one of these pricing models per event data store in CloudTrail Lake. One-year retention has a flat $0.75/GB ingest and cheap extension storage, and Seven-year retention has tiered ingest pricing but includes storage up to 7 years.
- Querying (CloudTrail Lake): When you run queries on CloudTrail Lake (or use CloudTrail’s natural language query feature), you pay for the data scanned by the query. This is charged similarly to Athena: $0.005 per GB scanned by your queries . For example, scanning 1 TB of data would cost roughly $5. (If you use Athena directly on S3 CloudTrail logs, you’d pay Athena’s query cost which is in the same ballpark.)
- Ingestion:
- Other Considerations:
- There is no minimum fee or setup charge for CloudTrail – you pay only for what you use . If you use multiple accounts, remember that creating an Organization trail (one trail for all accounts) can be more cost-effective than many individual trails. Also note that if the same event is delivered multiple times (say an org-level trail and an account-level trail both log the same event), the duplicates beyond the first copy are considered additional and billed . AWS also imposes some limits (like a maximum number of trails per region, etc., though those don’t typically incur cost). Always refer to the official AWS CloudTrail pricing page for the most up-to-date prices and details, as AWS occasionally updates pricing or introduces new features that could affect cost.
To put it simply: CloudTrail’s basic auditing is free, but if you start logging data-heavy events or want advanced analysis features, costs can accrue. For professionals, it’s key to architect your logging strategy (which events to log, where to store them, how long to retain) to balance visibility with cost.
Conclusion
AWS CloudTrail is a foundational service for anyone managing resources on AWS. It provides transparency into the actions taken in your cloud environment—a critical requirement for security, compliance, and operational troubleshooting. By understanding CloudTrail’s capabilities—from basic event history to advanced CloudTrail Lake queries—and how these differ from monitoring services like CloudWatch, you can design an effective logging strategy.
For beginners, enabling CloudTrail and sending logs to an S3 bucket is a straightforward way to start securing your AWS account. For seasoned DevOps engineers, CloudTrail serves as the data backbone for auditing and can be integrated with various tools and workflows to enhance your cloud governance. Always pay attention to what’s being logged, and review the AWS documentation for the latest features and best practices. AWS continues to enhance CloudTrail (for instance, through recent additions like network activity events for VPC endpoints), making it an ever more powerful tool in your cloud toolkit.
Optimize Your Cloud Expenses with Cloudchipr
Setting up AWS CloudTrail is only the beginning—actively managing cloud spend is vital to maintaining budget control. Cloudchipr offers an intuitive platform that delivers multi-cloud cost visibility, helping you eliminate waste and optimize resources across AWS, Azure, and GCP.
Key Features of Cloudchipr
Automated Resource Management:
Easily identify and eliminate idle or underused resources with no-code automation workflows. This ensures you minimize unnecessary spending while keeping your cloud environment efficient.
Receive actionable, data-backed advice on the best instance sizes, storage setups, and compute resources. This enables you to achieve optimal performance without exceeding your budget.
Keep track of your Reserved Instances and Savings Plans to maximize their use.
Monitor real-time usage and performance metrics across AWS, Azure, and GCP. Quickly identify inefficiencies and make proactive adjustments, enhancing your infrastructure.
Take advantage of Cloudchipr’s on-demand, certified DevOps team that eliminates the hiring hassles and off-boarding worries. This service provides accelerated Day 1 setup through infrastructure as code, automated deployment pipelines, and robust monitoring. On Day 2, it ensures continuous operation with 24/7 support, proactive incident management, and tailored solutions to suit your organization’s unique needs. Integrating this service means you get the expertise needed to optimize not only your cloud costs but also your overall operational agility and resilience.
Experience the advantages of integrated multi-cloud management and proactive cost optimization by signing up for a 14-day free trial today, no hidden charges, no commitments.

.png)
.png)
.png)