Choosing Hybrid Cloud Providers: A Practical Playbook
.png)
Introduction
You don’t move everything to “the cloud”; you decide what belongs where—and make the pieces talk cleanly. That’s the point of hybrid: two or more environments (often your data center plus a public cloud) behaving like one system. Place latency-sensitive or regulated workloads on-prem, burst the rest to cloud, and keep a single operational story.
What It Is & When To Use It
Hybrid cloud connects on-prem/private environments with public cloud services under one operational story—shared identity, policy, networking, and observability. You reach for it when you need:
- Low latency or local processing next to factories, clinics, or trading floors. (Running services on-prem while still using cloud APIs.) AWS Outposts is the canonical example here.
- Regulatory or data-residency constraints where data must remain on site but analytics can burst to cloud. Azure Arc and Google’s Distributed Cloud (formerly Anthos bare metal) are built to span that gap.
- Gradual modernization—lift pieces to the cloud while older systems keep humming in the rack room.
In short: if compliance, latency, or data gravity pull you on-prem, but you still want cloud operations and services, hybrid makes sense.
How It Works
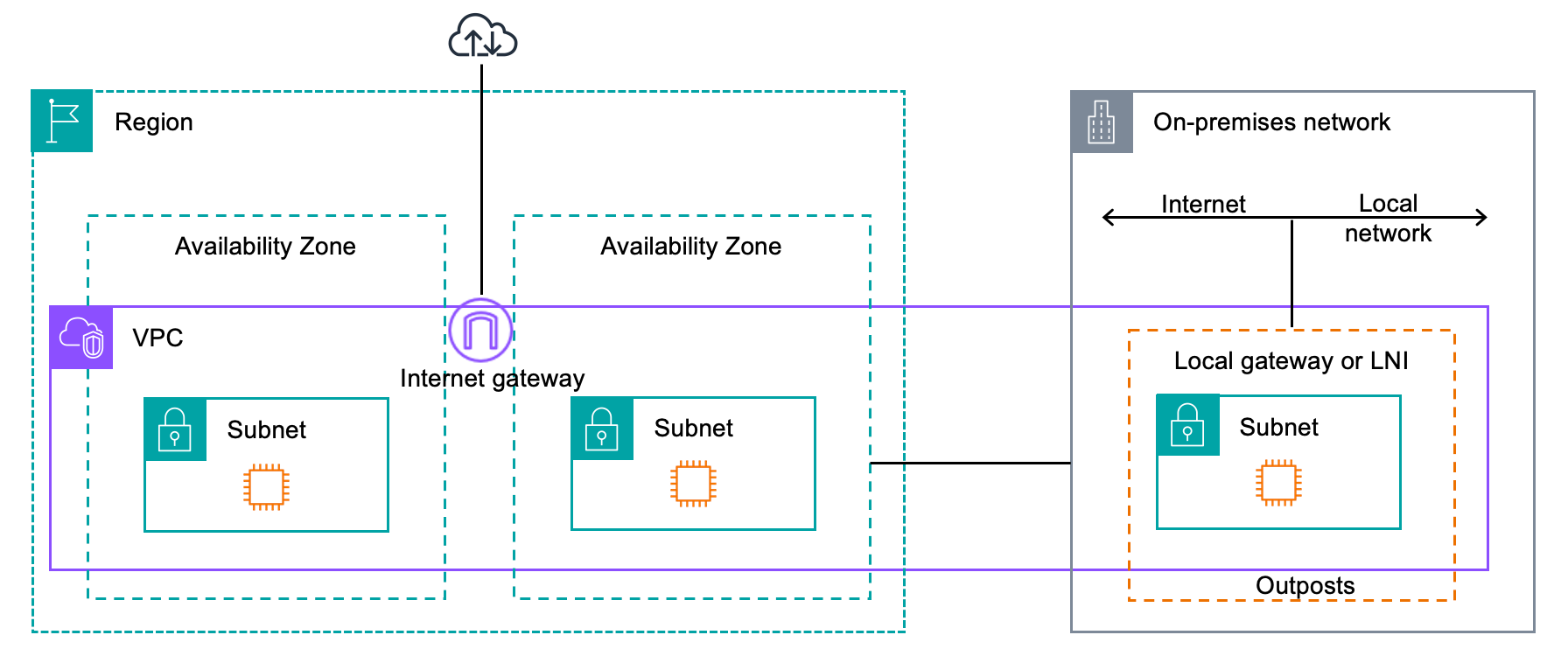
Imagine a retailer. Point-of-sale runs on-prem for sub-10ms response; inventory analytics runs in the cloud.
- Control plane: Register on-prem servers and K8s clusters with Azure Arc to apply RBAC, tags, and policy—just like native Azure VMs.
- Compute + services at the edge: Place AWS Outposts racks in stores/DCs to run EC2/RDS locally using the same AWS APIs you already know.
- Container platform option: Use Google Distributed Cloud (software-only) to run GKE on bare metal in your DC, managed from Google Cloud.
- Network: Private connectivity (Direct Connect, ExpressRoute, or Cloud Interconnect) ties sites to the cloud without hair-pinning over the public internet.
The user experience stays consistent; your ops teams get one policy surface, one logging story, and one CICD pipeline pointed at many footprints.
Implementation Steps
Pick the control plane: Decide whether your “single pane” lives in AWS (Outposts + AWS Organizations), Azure (Arc), or Google (Distributed Cloud/Anthos). This influences IAM, policy, and day-2 ops.
Design the network early: Choose private connectivity: AWS Direct Connect, Azure ExpressRoute, or Google Cloud Interconnect. Budget for port hours and egress (data transfer out).
Standardize the platform: Containers + Kubernetes simplify portability; Arc-enabled K8s or GKE/DC give you consistent deployment targets.
Plan data movement: Decide which data sets are authoritative on-prem vs. cloud; use services like AWS DataSync for scheduled, bandwidth-aware transfer.
Choose storage with hybrid in mind: Hybrid cloud storage providers like NetApp, Dell APEX, HPE GreenLake, and Pure offer consistent file/object services across on-prem and clouds—a big win for migrations and DR
Automate guardrails: Use policy-as-code, IaC, and cost controls from day one. Azure Arc exposes Azure Policy to non-Azure machines; same idea with organizational SCPs on AWS.
Observability + SRE baselines: Centralize logs/metrics/traces; test failure modes over private links (circuit down? route drift?).
Trade-offs & Common Pitfalls
- Egress surprises. Inbound to cloud is typically free; outbound is not. Expect per-GiB charges from hyperscalers; numbers vary by region and tier. (AWS examples place internet egress in the ~$0.08–$0.12/GB band; Google and Azure document region-based rates.)
- Port-hour “always on” costs. Private links (DX/ExpressRoute/Interconnect) bill per hour even when idle—plus data transfer. Budget both.
- Policy drift. Two environments, one set of controls—if you don’t unify IAM and policy, you’ll chase exceptions forever. Arc’s policy, for instance, helps keep non-Azure servers aligned.
- Storage sprawl. Multiple vendors, different snapshots, and conflicting retention. Prefer platforms that keep APIs and snapshots consistent across footprints.
Pricing & Cost Considerations
Hybrid isn’t automatically cheaper; it’s controllable if you know where the meters spin.
- Data transfer: Ingress is free; egress costs. AWS notes internet egress tiers and explicitly calls out Direct Connect as port-hour + DTO (data transfer out). Azure lists inter-region data transfer prices; Google documents per-GiB egress with Standard vs Premium network tiers.
- Private connectivity:
- AWS Direct Connect: pay per-hour for the port + egress
- Azure ExpressRoute: metered and unlimited plans; port fee applies, with data included on unlimited.
- Cloud Interconnect: per-hour per circuit + per-hour per VLAN attachment.
- Storage: S3/Blob/GCS storage rates are straightforward; your real cost can be reads/writes, retrieval tiers, and cross-region moves.
- Managed platform fees: Hybrid cloud managed service providers (MSPs) like Rackspace, IBM Consulting, and Accenture bundle operations and governance—often worth it for lean teams, but it’s an extra line item.
Who Fits Where?
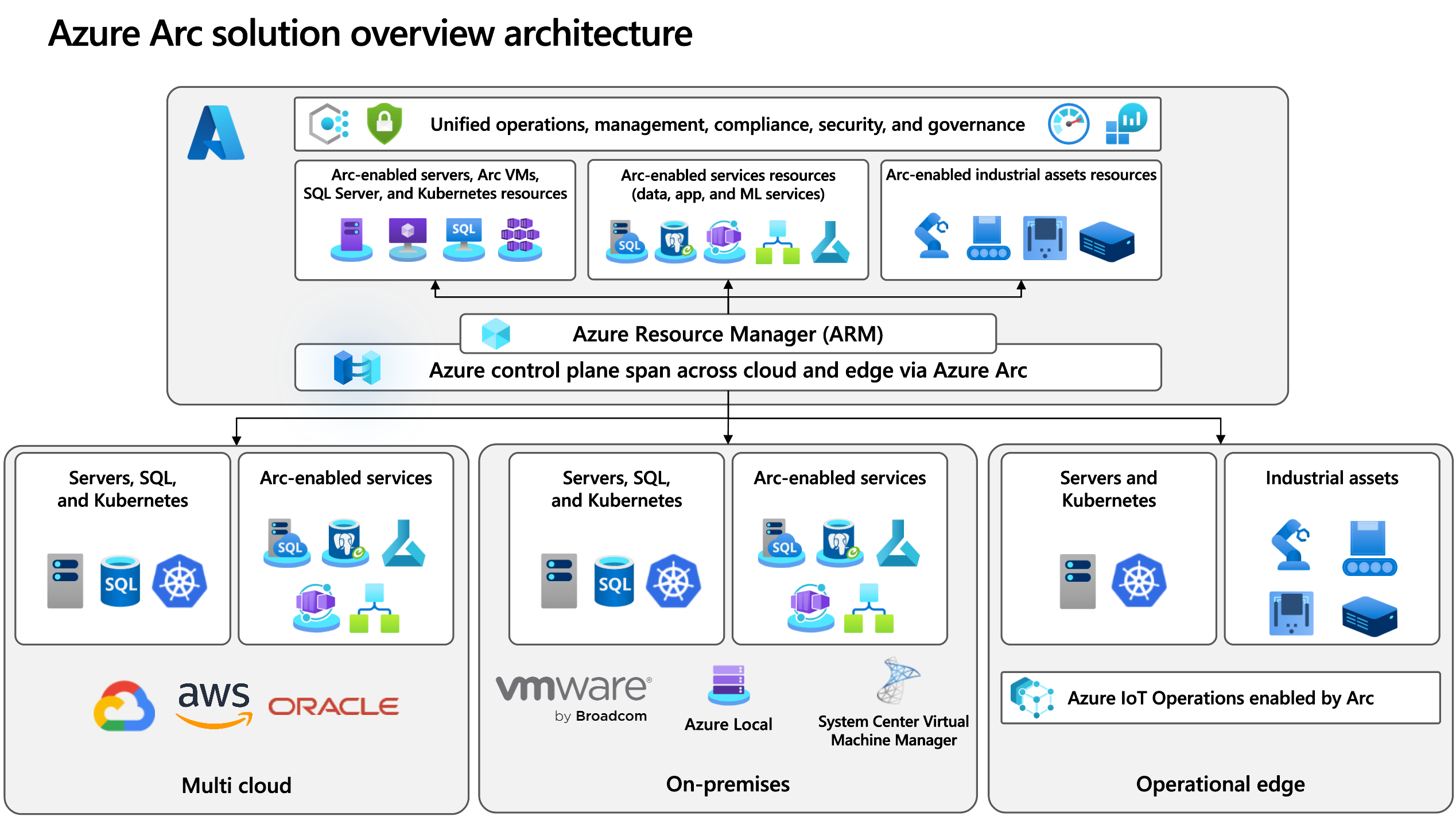
- AWS (Outposts family): native AWS services on-prem with region-consistent APIs. Great when teams are already deep on AWS.
- Microsoft Azure (Arc): bring non-Azure servers and clusters under Azure control; push Azure services to Arc targets. Use when Azure is your governance center.
- Google Cloud (Distributed Cloud/Anthos): GKE everywhere with central fleet management; strong K8s posture.
- Hybrid cloud storage providers (NetApp, Dell APEX, HPE GreenLake, Pure): consistent data services from rack to region.
- Hybrid cloud managed service providers (Rackspace, IBM Consulting, Accenture): operations, SLAs, and cost governance across estates.
Are these the best hybrid cloud providers? “Best” depends on your control plane choice, compliance needs, and where your engineering muscle already lives.
Best Practices (and a quick checklist)
- Start with data classification and network topology. Movement patterns drive cost.
- Pick one policy/identity backbone and apply it everywhere (e.g., Arc policy to non-Azure machines).
- Make egress a first-class metric in dashboards; alert when cross-boundary bytes jump.
- Keep storage platform-consistent to simplify DR and migrations.
- Prove resiliency over private links—simulate circuit failures quarterly.
Checklist to copy-paste into your runbook
- [ ] Control plane chosen (AWS/Azure/Google)
- [ ] Direct Connect / ExpressRoute / Interconnect sized & priced
- [ ] Identity & policy unified
- [ ] Storage platform picked (supports on-prem + cloud)
- [ ] Data flows mapped (ingress/egress measured)
- [ ] IaC and policy-as-code in place
- [ ] Observability centralized; chaos test run over private links
FAQ
Q1: Hybrid vs multi-cloud—what’s the difference?
Hybrid refers to binding different cloud infrastructures (public/private/on-prem) into one—often including your data center. Multi-cloud means using multiple public cloud providers. You can be both, but you don’t have to be.
Q2: Do small teams need hybrid cloud managed service providers?
Not always. If you’ve got mature platform/SRE practices, you can run it yourself. If not, MSPs (Rackspace, IBM Consulting, Accenture) cover ops and governance while you focus on apps.
Q3: Biggest cost gotcha?
Hands down: data egress and interconnect port hours. Model both before you move a byte.

.png)
.png)
.png)