AWS Cognito Essentials: Everything You Need for Authentication and Identity
.png)
Introduction
Amazon Cognito is a fully managed service from AWS that provides authentication, authorization, and user management for web and mobile applications. It allows developers to easily add user sign-up, sign-in, and access control features to their apps without building them from scratch. With Amazon Cognito, you get a secure user directory that can scale to millions of users and supports login through social identity providers (like Google, Facebook, Apple) or enterprise identity providers via SAML/OpenID Connect . In essence, Amazon Cognito acts as a cloud Identity and Access Management (IAM) service for your application’s users – handling the heavy lifting of user authentication and session management, so you can focus on your app’s functionality.
Cognito is part of AWS’s Customer Identity and Access Management (CIAM) solutions, meaning it’s designed to manage customer identities at scale with high security. It offers features like multi-factor authentication (MFA), risk-based adaptive authentication, and compliance-focused capabilities out-of-the-box. Cognito is also cost-effective for large user bases, with a generous free tier and low pay-as-you-go pricing that can be an order of magnitude cheaper than many competing identity services . In the sections below, we’ll explore how Amazon Cognito works, its key components, use cases, security features, integrations, pricing, and more, in a tutorial-style format that’s accessible to beginners and informative for advanced users.
Key Components of Amazon Cognito

Amazon Cognito comprises two main components (user pools and identity pools) and related features that work together to manage identities and permissions:
- Cognito User Pool: An Amazon Cognito user pool is a user directory and identity provider that manages your app users’ sign-up and sign-in processes . It stores user profiles (with customizable attributes), handles authentication (verification of passwords or social/SAML logins), and issues JWT tokens for authenticated users. From the perspective of your application, a user pool behaves like an OpenID Connect (OIDC) identity provider – with added features such as account verification (email/phone confirmation), password recovery, custom authentication flows via AWS Lambda triggers, and user interface customization. You can allow users to sign up directly with email/username and password, or federate users through external identity providers (e.g., sign-in with Google, Facebook, Amazon, Apple, or corporate SAML/OIDC providers) – the Cognito user pool will unify these into a single user directory and session token format . All members of a user pool have a directory entry that you, as a developer, can manage through the Cognito console or APIs.
- Cognito Identity Pool (Federated Identities): An Amazon Cognito identity pool (often called Federated Identities) is a mechanism to grant users temporary AWS credentials after they have authenticated, so they can access AWS services directly . Identity pools are not for authentication per se, but rather for authorization and identity federation. When a user is authenticated (via a Cognito user pool or any external IdP like Google, Facebook, Amazon, Apple, Twitter, or a SAML/OpenID provider), an identity pool can accept the proof of that identity (e.g. a Cognito token or a Google OAuth token) and exchange it for a set of AWS access keys (via AWS Security Token Service). You can think of the identity pool as a directory of federated identities each with a unique identifier and linked to one or more login providers. Using IAM roles and policies, you define what permissions those credentials have. For example, an identity pool can be configured to grant an “authenticated” role (with certain AWS permissions) to users who sign in, and a limited “guest” role to unauthenticated users . This allows scenarios like guest access (e.g., a user browsing an app without logging in can still fetch public data from S3 via the guest credentials) and elevated access for logged-in users (e.g., only signed-in users can write to a DynamoDB table). Identity pools support a variety of identity providers and will issue a consistent AWS identity ID for each user, enabling a unified experience across devices and login methods . In summary, if a user pool answers “Who is the user and are they authenticated?”, the identity pool answers “What AWS resources can this user access (with temporary creds)?”.
- User Groups and Roles: Within a user pool, you can create user groups to organize and manage your users. Groups are often used to represent roles or cohorts of users (e.g., “Admins”, “Editors”, “Customers”) and can have an associated IAM role to delineate permissions . When a user in a Cognito user pool belongs to a group that has an IAM role attached, that role’s ARN is embedded in the user’s token. If you integrate with an identity pool, the identity pool can automatically pick up that role to assign AWS credentials with the specified permissions to the user upon login . This provides a form of role-based access control (RBAC). Groups make it easier to manage authorization in your app as well – for example, your backend can read a user’s JWT token to see their cognito:groups claim and determine if they should have admin privileges in the application. There is no extra cost to use user pool groups, and you can manage group membership via the console, CLI, or admin APIs (adding/removing users from groups, listing group members, etc.) . AWS Cognito User Groups are a powerful way to map application-level roles to IAM roles, achieving fine-grained access control both within your application and to AWS resources.
(Other components:) In addition to the above, Cognito user pools involve App Clients (representing the applications that can call the user pool, each with a client ID/secret and configurable authentication flows), Identity Providers (configurations to enable logins from external IdPs like Google or Okta), and Lambda triggers (hooks that let you run custom code at certain events, such as during sign-up, token generation, authentication challenge, etc., to extend Cognito’s functionality). These components work together to provide a flexible authentication ecosystem. But the core concept is: user pools = authentication and user identity, identity pools = federated authorization to AWS.
AWS Cognito User Pool vs Identity Pool

One of the fundamental concepts in AWS Cognito is understanding the distinction between User Pools and Identity Pools. Each component plays a unique role within your authentication and authorization flow, and clarifying these differences early on will help you architect your solution effectively:
- Purpose: An AWS Cognito User Pool is a fully managed user directory and authentication service. It’s all about identifying and verifying users. It stores user credentials (hashed passwords, etc.) and profile attributes, and handles sign-ups, logins, and generating JWT tokens to represent the user’s identity and auth status. In contrast, an Amazon Cognito Identity Pool is used for authorizing access to AWS resources. It doesn’t store user accounts or passwords. Instead, it acts as a broker that takes identities from a user pool or external IdP and returns temporary AWS credentials (Access Key, Secret, Session Token) with permissions you define.
- Analogy: A user pool in Cognito is analogous to services like Auth0 or Firebase Authentication – it’s where you manage users and authenticate them . An identity pool is unique to AWS; it’s like a bridge between an identity provider (which could be Cognito user pool, social login, etc.) and AWS IAM. If you don’t need users to directly access AWS services, you might only use a user pool. If you do need AWS access, you will use an identity pool in conjunction (with some identity provider feeding into it).
- Data vs Credentials: User pools issue JWT tokens (ID token, access token) after a user logs in. These tokens are meant to be consumed by your application or other services for authentication/authorization. Identity pools issue AWS STS credentials (which have an IAM role’s permissions attached). Those credentials are used to sign AWS API requests. The identity pool itself also generates a unique identity ID for each user (a UUID tied to the user + identity provider). But identity pools do not know the user’s profile info or group memberships except what is passed in tokens; that heavy-lifting is done by the user pool or external IdP. Summarily: User Pool = tokens about who the user is; Identity Pool = credentials for what the user can access.
- Federation differences: User pools can federate multiple logins into one user (linking identities), but that user is always within the Cognito user pool (except for guest users, which user pools don’t handle). Identity pools can federate identities without a user pool – for example, you can use Identity Pool to let users login with Facebook and Amazon without ever creating a Cognito user account, and still get AWS creds. Identity pools also support the concept of “unauthenticated user” (guests) natively. User pools by themselves have no concept of guest – a user either exists or not.
- When to use which: If your goal is to handle user sign-up/sign-in and manage user accounts (with emails, passwords, etc.) for your app, use a User Pool. If your app (usually a mobile or client-side app) needs to directly call AWS services (like S3, DynamoDB, etc.) using users’ permissions, use an Identity Pool (with some identity provider feeding it – often that’s a Cognito user pool). In many scenarios you actually use both together: the user pool manages the user’s authentication and then provides tokens to the identity pool for AWS access . However, you can use user pools alone (for example, a web app that only needs JWTs to authenticate users to your backend and doesn’t require any AWS resource access from the client side). You can also (less commonly) use identity pools alone with social providers for a pure federated access use case (e.g., an appliance device that just needs AWS IoT access via Google login).
To avoid confusion: Cognito = User Pools + Identity Pools.
They are separate in function but complementary. AWS often uses the term “Amazon Cognito Federated Identities” to refer to identity pools and “Amazon Cognito User Pools” for the user directory. A helpful way to remember: User Pool = Users (authentication), Identity Pool = Identities for AWS (authorization).
In the context of an application, user pools handle the front-door login and identity confirmation, while identity pools handle obtaining AWS IAM roles for those identities. You can certainly use one without the other depending on your needs. But if you use both, Cognito provides an end-to-end solution from user login UI to AWS resource access control.
How It Works (Authentication Flow)

Cognito authentication flow: A typical Amazon Cognito user authentication flow involves (1) the user authenticating against a User Pool (user directory) to obtain tokens; (2) optionally exchanging those tokens via an Identity Pool for temporary AWS credentials; and (3) using those credentials to access AWS services (if required by the application). Amazon Cognito handles the multi-step authentication flow for you – including third-party logins, delivering MFA challenges, and token issuance – so that your application only needs to process the outcome (the tokens or credentials).
In practice, when a user logs in, Cognito verifies their credentials (for example, via a hosted Cognito sign-in page or an SDK in your app). If the login is successful, Cognito establishes a session and returns a set of JSON Web Tokens (JWTs): an ID token (with the user’s identity claims like username, email, etc.), an access token (with scopes or permissions for authorized calls), and a refresh token. These tokens are automatically issued over a secure channel and represent the user’s authenticated session. Your application can use the ID or access token to authenticate requests to your backend services or to AWS API Gateway (for example, using Cognito’s JWT to authorize API calls). If your app needs direct AWS access (such as uploading to Amazon S3 or invoking a Lambda), the Cognito Identity Pool comes into play: your app can take the Cognito user pool token and exchange it for temporary AWS credentials via the identity pool . Those AWS credentials are scoped by IAM roles that you configure, ensuring the user only accesses allowed resources. All of this happens via secure protocols (Cognito user pools are OIDC-compliant identity providers), and AWS SDKs (or the Amplify library) can abstract the token exchange process for you. In summary, Amazon Cognito streamlines authentication by providing tokens for user identity and (when needed) AWS credentials for resource access – covering both authentication (verifying who the user is) and authorization (what the user can access) steps in one integrated flow.
Use Cases for Amazon Cognito

Amazon Cognito is versatile and can be applied to a variety of identity management scenarios. Some common use cases include:
- User Authentication for Web & Mobile Apps (B2C): Cognito is often used to manage customer logins for consumer-facing applications. For example, a mobile app can use Cognito User Pools to let users sign up with email or social login and handle all the verification, password resets, and MFA, providing a smooth onboarding experience. The app developer benefits by not having to store passwords or build a login backend from scratch – Cognito provides a secure authentication service out of the box.

- Secure Access to AWS Resources in Apps: If you are building an application that needs to interact with AWS services on behalf of users (for instance, a photo sharing app where users upload images to a private S3 bucket, or an IoT application where devices send data to AWS IoT or DynamoDB), Cognito’s identity pools are a perfect fit. You can give each user a limited set of AWS credentials via an identity pool so that they can directly access the allowed AWS resource. This avoids embedding long-term AWS keys in the app. For example, a game application can use Cognito to obtain temporary AWS credentials for players, allowing the game to save high scores in DynamoDB or download level data from S3 securely.

- Social and Enterprise Single Sign-On: Cognito makes it straightforward to offer Single Sign-On (SSO) options to your users. A common use case is allowing users to log in with their existing identities – such as Google, Facebook, Apple IDs for social login, or with corporate credentials via SAML federation (e.g., logging in with an Azure AD or Okta account). Cognito user pools can federate multiple identity providers and unify the users into a single user pool, improving user experience (one account can be linked to several login methods) while your application deals with a single set of Cognito tokens. This is useful for applications that want to reduce password fatigue or integrate with enterprise customers’ SSO requirements. For instance, a SaaS application could let employees from different client companies log in using their company’s SAML SSO – Cognito will trust those external IdPs and still create a user record for each employee in the user pool.
- Business-to-Business (B2B) and Multi-Tenant Apps: For applications that serve multiple business clients (tenants), Cognito provides mechanisms to manage identities in a multi-tenant fashion. You might create separate user pools for each tenant or use groups/attributes to separate users within one user pool. Cognito’s ability to define groups and roles can help implement tenant-specific roles. AWS even allows setting up Cognito to integrate with different SAML IdPs for different user groups, enabling each business to use its own identity provider. This flexible identity federation is a big use case for B2B SaaS platforms.
- Enhanced Security and Compliance: Applications in sensitive domains (finance, healthcare, etc.) use Cognito to leverage advanced security features like MFA, adaptive authentication, and audit logging to meet compliance requirements. For example, you can enforce MFA for all users or only for high-risk logins, use Cognito’s built-in compromised credentials check to detect if a user’s password was found in a public breach database, and maintain an audit trail of sign-in attempts. Cognito is compliant with various security standards and can help your app adhere to policies (it can enforce password complexity, lock out users after X failed attempts, etc.). These features make Cognito suitable for enterprise-grade applications where security is paramount.
In summary, Amazon Cognito can be used anywhere you need to manage user identities and authentication at scale, especially if your application runs on AWS. Whether it’s a simple user sign-up for a blog, a large-scale mobile app with millions of users, or an enterprise application requiring SSO and fine-grained AWS access, Cognito provides a toolkit to implement these scenarios with minimal custom code.
Amazon Cognito Multi-Factor Authentication (MFA) and Security Features

Security is a major focus of Amazon Cognito. One key feature is multi-factor authentication (MFA), which adds an extra layer of protection on top of the username/password login. With Cognito, you can configure MFA in various modes: it can be Optional (users can choose to enable it) or Required (all users must use MFA) for the user pool. Cognito supports using SMS one-time passcodes, time-based one-time passwords (TOTP) from authenticator apps (like Google Authenticator or Authy), and even email one-time codes as MFA factors . For example, you could set MFA to optional and let users enroll an authenticator app for a 6-digit code, or set MFA required so that every login requires a second factor. If MFA is required, Amazon Cognito will automatically prompt new users to configure an MFA device at first sign-in and will enforce MFA on every subsequent login . This is a simple switch in the user pool settings, and the Cognito hosted UI will handle the MFA challenge workflow for you. (If you build a custom UI, the AWS SDKs also expose the challenge steps so you can implement the prompt for an MFA code.) Note that for federated users (who log in via SAML or social providers), Cognito defers MFA to the identity provider – e.g., if a user logs in with Google which has its own 2FA, Cognito will accept that and not double-prompt.
Beyond MFA, Amazon Cognito offers advanced security features (now called “Threat Protection”) to protect user accounts and your application. These include: Compromised Credentials Check, which uses threat intelligence to detect if a user’s credentials might have been leaked elsewhere – if a user’s chosen password appears in known data breaches or is too common, Cognito can block it or force a reset . There’s also Adaptive Authentication, which is a risk-based system that evaluates context like device fingerprint and IP address geo-location for each sign-in attempt . If a login is deemed risky (e.g., a user logging in from a new country or an unusual device), Cognito can automatically either prompt for MFA or block the login, according to policies you set . These adaptive controls greatly reduce the chance of account takeover. Additionally, Cognito allows you to setup IP allow/Deny lists to explicitly block certain IP ranges , and it provides detailed logging of sign-in attempts and risk scores to CloudWatch for audit purposes .
Other security capabilities include enforcing strong password policies (min length, require symbols/numbers, etc.), email/phone verification for sign-ups (to ensure ownership of contact info), and the ability to enable encryption at rest for user data by default. Also, since Cognito is an AWS service, all communication with it is over HTTPS and it inherits AWS’s compliance certifications (SOC, ISO, PCI DSS, etc.). As a developer, you can further secure Cognito integration by using features like SRP (Secure Remote Password) protocol for the AWS SDK-based sign-in (which ensures the actual password is never sent over the network, even encrypted). In summary, Amazon Cognito provides robust security features – MFA for an extra layer of auth, and advanced threat protection measures – to help safeguard your users and meet high security standards.
AWS Cognito SSO and Federated Identities

Amazon Cognito is often used to enable Single Sign-On (SSO) experiences, leveraging its support for federated identities. AWS Cognito SSO typically means using Cognito User Pools as the central identity provider for multiple applications or allowing users to authenticate through an external SSO provider into Cognito. Cognito user pools can be configured to federate with a variety of external identity providers – including popular social logins and enterprise IdPs. For social logins, Cognito has built-in integrations (referred to as identity federation) for providers like Google, Facebook, Amazon, Apple, and Twitter. You can also set up Cognito to trust any OIDC-compliant IdP or SAML 2.0 IdP . This means if your users already have identities in an external system (for example, G Suite/Google Workspace, Azure AD, Okta, or any SAML identity service), you can let them use those credentials to sign into your application via Cognito. Cognito will handle the SSO handshake (SAML assertion or OIDC token exchange) and then create a user entry in the user pool (if you choose to auto-provision) or just authenticate the user without a password. From the application’s viewpoint, all users – whether they came from a local sign-up or via SSO – are represented by Cognito tokens. This unification is very powerful: it enables scenarios like bring-your-own-identity (users don’t need to make a new password for your service) and enterprise federation (letting users use corporate SSO to access a SaaS app, while you still manage them in Cognito with specific app permissions).
Cognito supports SAML 2.0 federation extensively. For instance, you can configure a user pool as a SAML Service Provider, which means it will accept SAML responses from an IdP. Many companies use this to integrate Cognito with their internal user directories for B2B apps. OpenID Connect federation is similarly supported – any IdP that supports OIDC (which includes most modern identity services) can be integrated. By configuring identity provider integrations in the Cognito console or via CloudFormation, you essentially tell Cognito: “trust identities from this provider”. After that, Cognito’s hosted UI will show a “Continue with XYZ” button, and users can authenticate through that provider. All the identity assertions (like user attributes from the IdP) can be mapped to Cognito user attributes. In summary, Amazon Cognito federated identities feature of user pools allows you to plug in external SSO sources easily , achieving single sign-on across your and third-party applications.
On the other side of the coin, Cognito Identity Pools provide SSO into AWS resources. When using identity pools, you can accept identities from Cognito user pools or directly from external IdPs (even if you don’t use a user pool at all in between). For example, you could let users sign into your mobile app with Facebook, and without creating a user pool, pass the Facebook OAuth token to a Cognito Identity Pool. The identity pool will map that to an “authenticated role” and give AWS credentials. In this way, identity pools act as a broker that trusts many identity providers and funnels them into AWS IAM roles . This is often used for backend resource access: your app can call AWS services on behalf of a federated user (be it a Cognito user, a Google user, etc.). The identity pool treats a Cognito User Pool just as one more external IdP in its configuration. When a user pool and identity pool are used together, you achieve a full OAuth + AWS credential flow: Cognito user pool provides the initial auth and a unified identity token, and the identity pool exchanges it for AWS credentials. As AWS’s docs put it, “Amazon Cognito user pools are like OIDC identity providers to your SSO-enabled apps. Identity pools act as an AWS identity provider to any app with AWS resource access.” In simpler terms, use user pools for SSO into your application (including federating external users into it), and use identity pools for SSO into AWS.
To illustrate an example: imagine a web application that has its own user base but also wants to allow corporate users from client companies to SSO. You could set up a Cognito user pool and configure multiple SAML IdPs (one for each client’s ADFS/Okta). All those users can authenticate via their respective SSO and will appear in your user pool. Now, suppose your app also lets users upload files to a private S3 bucket per user. By integrating an identity pool, when any user (local or federated) logs in, you exchange their user pool token for AWS credentials that allow access to their segment of S3. The user seamlessly uses the app with SSO and also securely accesses AWS resources, without ever handling AWS credentials directly. This seamless bridging of identity is a strong suit of Cognito.
.png)
AWS Cognito API and User Management
Amazon Cognito provides extensive APIs and tools for user management and integration. After setting up a user pool, you will often need to perform administrative tasks on user accounts or integrate the user directory with your application logic. Cognito offers multiple ways to do this:
- Admin APIs: AWS provides an API (and corresponding AWS CLI commands and SDK methods) for managing users in a user pool. This is part of the AWS Cognito Identity Provider service (often referred to as “cognito-idp” in CLI). With these APIs, you can programmatically create users (AdminCreateUser), confirm or verify users, enable/disable users, set temporary passwords, force password resets, update attributes, and delete users. You can also list users or search for users by attributes (ListUsers with a filter, e.g. by email) . For example, an admin dashboard for your app could use these APIs to search for a user by email and disable their account if needed. The admin APIs require AWS credentials with appropriate permissions (e.g., an IAM role in your backend) – they are not exposed to end-users but rather used by your secure backend or administrative scripts.
- User Self-Service APIs: Cognito also exposes user-facing APIs (through SDKs or endpoints) that allow users to sign themselves up, confirm their sign-ups (with a confirmation code), initiate forgot-password flows, authenticate (initiate auth and respond to challenges), refresh tokens, etc. If you’re using AWS Amplify or the AWS Mobile SDKs, these methods are provided in a convenient way. For instance, in a JavaScript web app you might use Amplify Auth’s signUp, confirmSignUp, signIn methods which under the hood call Cognito’s endpoints. These self-service operations enforce all the user pool’s policies (like verification, MFA, password policies) automatically.
- Cognito Console and User Management UI: The AWS Management Console for Cognito provides a UI to perform many user management tasks as well. You can view the list of users in your user pool, their status (enabled, disabled, needs confirmation, etc.), and edit their attributes. You can manually create users (with or without sending them an invite email), confirm users, reset passwords, and even export user lists. The console is handy for quick operations or managing small numbers of users. However, for large-scale operations (imagine bulk-importing tens of thousands of users), you’d rely on APIs or import tools.
- Bulk User Import and Migration: If you have an existing user base in another system and you want to move to Cognito, AWS provides solutions for that. Cognito supports a CSV user import feature where you can upload a file with user data (this requires using AWS CLI or an AWS Lambda-based importer and has specific formats/limitations, such as only importing hashed passwords from specific algorithms). Alternatively, Cognito offers a user migration Lambda trigger: this is a custom Lambda function that runs when a user first tries to log in but is not found in the user pool – in that moment, your Lambda can verify the credentials against your old user store and then import/create the user into Cognito on the fly. This approach (just-in-time migration) allows a smooth transition without forcing all users to reset passwords at once . It’s quite powerful for migrating from another auth system (say, a custom database) to Cognito with minimal user disruption.
- User Attribute Management: Cognito user pools allow defining custom attributes (beyond the standard ones like email, phone, name). Through the API, you can update a user’s attributes or read them. For example, your app might set a custom attribute “userType=premium” for certain users; this could later be used in business logic or even to assign to a particular group. Both admin and users themselves (through the UpdateProfile functionality) can modify certain attributes (with proper permissions).
- Access Control and Policies: Using groups and IAM role mapping (as discussed earlier), you can manage fine-grained access. For instance, you can assign IAM roles to groups , and when users in those groups get AWS credentials via an identity pool, they receive the permissions of that role. This is managed in Cognito configuration but enforced via AWS IAM. Additionally, the tokens issued by Cognito carry information like group membership and can be used directly in your application’s authorization logic (for example, an isAdmin claim or group claim in the token tells your backend what the user can do).
All these capabilities mean that AWS Cognito user management can handle complex lifecycle scenarios: account provisioning, verification, login, password recovery, profile updates, and account deactivation. You can automate governance tasks as well – e.g., periodically disabling users who haven’t logged in for a long time, by using the ListUsers API with a filter on last modified date, etc. The scale is not a problem: Cognito user pools can scale to hundreds of millions of users, and the APIs are designed to be used in high-volume environments . And because it’s an AWS service, you can combine it with others – for example, use Amazon EventBridge or CloudWatch Events to trigger notifications on certain admin events, or use AWS CloudTrail logs for auditing changes to your user pool.
In summary, Amazon Cognito provides a rich set of APIs for both authentication workflows and administrative user management. Developers can integrate Cognito’s user directory into their apps using standard protocols (OAuth 2.0/OIDC flows) or AWS SDKs, and operators can manage the user base through AWS Console or programmatically with AWS infrastructure-as-code and scripts. This flexibility makes it suitable for both simple apps and large enterprise systems.
AWS Cognito Pricing
One of the attractive aspects of AWS Cognito is its pricing model, which can be very cost-efficient especially for apps with large numbers of users. AWS Cognito pricing is primarily based on Monthly Active Users (MAUs) for user pools, with a free tier that covers a substantial number of users. As of this writing, Amazon Cognito user pools offer a free tier of 50,000 MAUs per month for existing accounts (and 10,000 MAUs for new accounts under the updated pricing plan), which means if your application has up to that many active users in a month, you pay nothing for Cognito’s core authentication service. Beyond the free tier, the charges are tiered per MAU. Under the legacy pricing (which many accounts still benefit from), the rate is about $0.0055 per MAU after the first 50k users , and it gets slightly discounted at very high volumes (millions of users) . The new pricing introduced in late 2024 simplified this to tiers called “Cognito Lite, Cognito Essentials, Cognito Plus” with a rate roughly $0.015 per MAU after 10k free for the standard tier, but AWS grandfathered existing users to keep the lower rate for a period. In any case, the cost per user is a fraction of a cent in Cognito. For example, 100,000 monthly active users might incur only a few hundred dollars in Cognito fees, which is dramatically lower than many third-party identity providers that might charge on a per-user per-month basis in the range of dollars.
It’s important to note what counts as an “MAU”: generally, an MAU is a unique user who authenticates (or refreshes token) in that month. If the same user logs in multiple times, it’s still one MAU. This makes pricing predictable relative to your active user count.
Identity pools (Federated Identities) are free. Amazon Cognito identity pools do not themselves incur a charge for authentication or token exchange . You can have unlimited identity pool identities and the act of issuing AWS credentials via an identity pool is provided at no additional cost. You only pay for the AWS resources those credentials access (for example, if a user uses credentials to put an item in DynamoDB, you pay for the DynamoDB usage). The only potential cost related to identity pools is if you use the Cognito Sync feature (an older service to sync user data across devices) or Amazon Pinpoint analytics via identity pools, but those are separate services. So, using identity pools to grant AWS access has no direct fee, which is great.
There are a couple of additional charges to be aware of in Cognito:
- MFA SMS Messages: If you use SMS for sending MFA one-time passcodes or for user phone verification, those SMS messages are sent via Amazon SNS and charged separately per message (based on SMS rates to the destination country) . AWS Cognito will trigger the SNS service to send the text, and you’ll see those costs in your SNS usage. Similarly, sending emails (for verification codes, welcome messages, etc.) is done via Amazon SES — there’s a generous free tier for SES, but large volumes of emails might incur a small cost .
- Advanced Security Features: Cognito’s “Threat Protection” (compromised credential check and adaptive authentication) is priced as an add-on per MAU if you enable it. Under the old model this was ~$0.05 per MAU for the first 50k, etc., and under the new Plus tier, it’s included but at a higher base MAU price. Essentially, if you enable these advanced security features, there is an extra charge on top of the base MAU price . AWS transparently reports this as separate line items (“Advanced Security MAUs”).
To put it in perspective, for many applications Cognito will cost $0 because they won’t exceed the free tier (for example, a hobby app with 5,000 users won’t pay anything). For apps that scale to say 100k users, you might pay on the order of $300-$500 per month, which is often much less than competing services (Firebase Auth is free at that scale; Auth0 or Okta would charge significantly more on paid plans). AWS also does not charge extra for standard features like social identity federation – it’s all counted in MAUs. The cost scales linearly with usage, so you don’t get sudden jumps for crossing a tier (except after free tier).
Summary of Cognito Pricing:
- User Pool: Free for first 10k-50k MAUs, then a small fee per MAU thereafter (exact rates depend on plan, roughly $0.005–$0.015 per user). No expiration on the free tier – it’s not limited to 12 months, it’s perpetual .
- Identity Pool: Free (no direct charge for federated identities).
- Extras: Pay for SNS SMS (if used), SES emails (if high volume), advanced security (if enabled, per MAU fee).
Overall, AWS Cognito pricing is very startup-friendly and scalable. You can start for free and even as you grow, the costs remain predictable and usually much lower than rolling out your own identity solution (when you consider the development and maintenance effort) or using enterprise identity platforms. Always check the latest AWS pricing page for any updates or changes in rates, but as of 2025, Cognito remains one of the most cost-effective CIAM solutions on the market for B2C apps .
Amazon Cognito Tutorial / Walkthrough
In this section, we’ll walk through a simple Amazon Cognito tutorial to set up a user pool and identity pool, demonstrating the typical steps and how they tie together. This high-level walkthrough can serve as a guide for implementing Cognito in your own project:
- Create a User Pool: Log in to the AWS Console and navigate to Amazon Cognito. Under “User Pools”, click Create a user pool. Give the user pool a name (e.g., “MyAppUserPool”). You can choose the Quick start (default settings) for now or go through the detailed setup wizard to customize settings. (In detailed setup, you’ll configure sign-in options, security, etc. as described next.)
- Configure Sign-In Options: Decide how users will sign in. Cognito lets you allow usernames, email, or phone number as the sign-in identifier. For example, you might choose to allow sign-in with email (which is common). In the console wizard, under “How do you want your end users to sign in?”, you’d select email (and/or phone) as required. You can also enable self-registration so users can sign themselves up, or disable it if only admins will create users.
- Set Up Security Policies: In your user pool settings, configure password policy (minimum length, require numbers or symbols, etc.) according to your needs. Enable Multi-Factor Authentication (MFA) if desired – you can set it to Optional or Required. For this tutorial, you might set MFA to Optional and allow SMS and TOTP as second factors . Also, choose your account recovery method (email by default, or phone, or both). Cognito will handle sending verification codes for account recovery based on these settings.
- Define User Attributes: Specify what attributes you want to collect and store for users. By default, Cognito includes standard attributes like email, phone, name, etc. You can mark some as required (e.g., require email). You can also add custom attributes if your app needs them (for instance, “customerId” or “referralCode”). For a simple setup, you might just require email and perhaps phone number for contact. Cognito will ensure required attributes are provided at sign-up.
- Configure MFA and Verification Messages: If you enabled MFA or want Cognito to handle user sign-up verification, configure the messaging. Cognito can send verification codes via email or SMS. For example, verify email on sign-up: Cognito will email a code to new users. In the user pool console, you can customize the email/SMS templates (the code subject line, etc.). For low-volume, Cognito provides a built-in email sender; for production, you might integrate Amazon SES for branded emails. Likewise, ensure an SNS role is in place if using SMS (the console can create one for you).
- Create an App Client: A user pool requires an App Client which represents the application that will connect to Cognito. Go to “App clients” in your user pool and create a new app client (e.g., “MyAppClient”). You can choose to generate a client secret or not (for public client like JavaScript or mobile apps, no secret is typical). Note down the App Client ID (and secret if any). Under “App client settings”, you can also enable the Cognito Hosted UI for this client by assigning it a domain. For simplicity, let’s say you use Cognito’s default domain (you’ll get something like myapp.auth..amazoncognito.com). Configure allowed callback URLs (where Cognito will redirect after login, e.g., http://localhost:3000/callback if you’re testing locally) and sign-out URLs.
- Test User Sign-Up and Sign-In: At this point, your user pool is created. You can now test it. One way is to use the Hosted UI (Cognito’s built-in login page). Navigate to the hosted UI URL for your user pool’s domain (there’s a link in the console under Domain and the App client settings). It will show a sign-in page where you can switch to “Sign Up”. Try creating a new user through this interface – enter an email, a password, and any required info. Cognito will send a verification code to your email. Enter the code to confirm the account. Now sign in with the email and password. You should be redirected to the callback URL with tokens (if you set that up), or if you used the test interface, you might just see a JSON with your tokens. Congratulations – Cognito is now handling user registration and login! 🎉
- Set Up an Identity Pool (if AWS access needed): If your application needs to access AWS resources, create an Identity Pool. In the Cognito console, go to “Federated Identities” (or via AWS console search “Cognito Identity Pools”) and create an identity pool (e.g., “MyAppIdentityPool”). Enable Unauthenticated identities if you want guest access or leave it disabled if not. Most importantly, under “Authentication providers”, select Cognito and choose the user pool you created and its app client. This links the identity pool with your user pool as an auth provider. The wizard will prompt to create two IAM roles – one for unauthenticated and one for authenticated users. Accept the defaults (you can tweak the IAM policies later to grant specific permissions). Now, your identity pool can accept a Cognito user pool JWT and exchange it for AWS credentials .
- Integrate into Your Application: With the user pool and identity pool set up, integrate them into your app’s code. For example, using AWS Amplify in a JavaScript app, you would configure Amplify with the user pool ID, app client ID, identity pool ID, and region. Amplify’s Auth module would then let you call Auth.signUp, Auth.confirmSignUp, Auth.signIn, etc., to handle the user flow. After sign-in, Amplify (or the AWS SDKs) can automatically retrieve AWS credentials if an identity pool is configured, which you can then use to call services like S3. If not using Amplify, you can use the AWS Cognito SDK directly or even standard OAuth flows: direct your users to the Cognito hosted login URL, get the code, exchange it for tokens at Cognito’s /oauth2/token endpoint, then use AWS STS AssumeRoleWithWebIdentity for identity pool if needed. For brevity, the main point is that Cognito provides all the endpoints and SDK support to plug into your app with minimal effort. In our simple test, you might use the hosted UI as a quick way to validate everything: the tokens you received after sign-in can be decoded (they are JWTs) to see the claims, and if you configured an identity pool, you can use the AWS CLI or SDK with those tokens to get AWS temporary credentials.
- (Optional) Apply Advanced Settings: Once basic auth is working, you can explore more features: enable MFA in the user pool settings and test an MFA login (Cognito will walk the user through MFA enrollment). Set up a custom domain for the hosted UI for a branded login page. Create some user groups in the user pool (say “Admins”) and assign a user to the group, and attach an admin IAM role to that group so that when that user logs in and gets credentials from the identity pool, they have elevated AWS permissions. You can also implement Lambda triggers, for example, to add custom welcome email logic or to validate user-provided data at sign-up (like rejecting certain email domains). These steps depend on your specific requirements, but Cognito has the flexibility to accommodate them.
This concludes our basic walkthrough. We created a user pool, allowed a user to sign up and sign in, and (optionally) tied in an identity pool for AWS access. From here, you would incorporate this into your application’s authentication flow. For a complete tutorial, you might build a small demo app that uses Cognito for login, but the above steps are the core building blocks you’d use in any such implementation. Amazon Cognito’s documentation and AWS Amplify libraries provide further detail on coding the integration, but the setup you’ve done is the foundation for a production-ready authentication system.
Amazon Cognito vs Firebase
.png)
Both Amazon Cognito and Google Firebase offer solutions for user authentication and app backends, but they have different strengths. Let’s compare Amazon Cognito vs Firebase Authentication on key aspects:
- Cloud Ecosystem Integration: Cognito is tightly integrated with the AWS ecosystem, making it ideal if your application stack is on AWS. It seamlessly works with AWS services (via identity pools) and uses AWS IAM for access control . Firebase Authentication, on the other hand, is part of Google’s Firebase platform (and Google Cloud). It integrates naturally with other Firebase services like Firestore (database), Firebase Cloud Messaging, Google Analytics, etc. Your choice might depend on your overall cloud architecture – if you’re using a lot of AWS services, Cognito keeps everything in one place; if you’re building a mobile app heavily using Firebase’s realtime database, hosting, etc., Firebase Auth fits naturally with those.
- Features and Authentication Options: Both Cognito and Firebase support standard authentication methods (email/password sign-up, email link sign-in, social logins via Google/Facebook/Apple, etc.). Cognito additionally has built-in support for enterprise SAML and OIDC providers, which Firebase’s base product does not (Firebase Auth is more focused on social providers and custom JWT, whereas Google’s separate Identity Platform (a GCP service) would be needed for SAML). Firebase supports phone number authentication out-of-the-box, sending OTP codes via SMS as a login method, which is something Cognito user pools don’t directly provide as a primary sign-in method (Cognito uses phone for verification/MFA, but not as a password-less login identity except via custom flows) . Both services offer MFA: Cognito has MFA (TOTP/SMS) for user pools; Firebase recently introduced MFA (SMS-based) for phone/email sign-in as well. In terms of user management features, Cognito has more advanced policies (password policies, account locking, etc.), whereas Firebase keeps things simpler (relying on Google’s secure defaults). Cognito also allows customizing the JWT claims and using Lambda triggers to run custom logic during auth flows, which provides flexibility (for instance, you could implement complex validation or even custom challenge flows); Firebase Auth has less of that kind of extensibility on the Auth service itself (though you can always write Firebase Cloud Functions to react to auth events).
- Developer Experience: Firebase is often praised for its developer experience – it is generally considered very easy to integrate, especially for mobile and front-end developers. It provides straightforward SDKs and a unified console for not just auth but many other services. Cognito has improved over time (and AWS Amplify greatly simplifies using Cognito in front-end apps), but developers sometimes find Cognito’s setup more complex or its documentation less beginner-friendly. For example, setting up a custom domain or dealing with user pool vs identity pool can be confusing initially. Firebase’s documentation and community might be a bit more approachable for new developers, and it has a large active community (Firebase being used in many hobby and startup projects) . That said, Amplify CLI and libraries do make Cognito integration fairly easy as well, but with AWS you have the power (and complexity) of AWS IAM and other config in the mix.
- Pricing: Both Cognito and Firebase have generous free allowances and scalable pricing. Firebase Authentication is free for essentially unlimited users for email/password and social logins – there is no charge per user; however, if you use phone auth, Firebase charges a small fee after a certain quota of SMS sends. Cognito, as discussed, gives a large free MAU tier and then charges per MAU beyond. In real terms, for 100k active users, Firebase and Cognito would both be very low cost (Firebase would still be in free tier except for phone verifications; Cognito would charge a few hundred dollars) . Firebase’s free tier is attractive for new apps (and you only pay for other Firebase services as you use them). Cognito’s costs might kick in only when you have substantial usage, and even then it’s pay-as-you-go without needing to choose a plan. If your app is already using Firebase’s database/hosting, using Firebase Auth doesn’t add cost. If you’re on AWS, using Cognito likely saves you from the cost of adopting a third-party auth service. Overall, pricing is a minor point since both are affordable at scale (Cognito’s old pricing of $0.0055/MAU is roughly matched by Firebase’s model when you cross certain thresholds ).
- Additional Capabilities: Cognito offers some things Firebase doesn’t, notably the direct AWS IAM integration (Firebase cannot give users AWS credentials obviously) and advanced security features like adaptive authentication, which are not part of Firebase Auth. Conversely, Firebase, as a platform, offers many adjacent services (Firestore, Functions, Storage, etc.) which integrate with Firebase Auth for security rules (for example, in Firestore you can write rules based on auth.uid). If your goal is a quick serverless app backend with minimal setup, Firebase’s suite might get you there faster (at the cost of being tied into Google’s ecosystem). Cognito is more standalone for auth but pairs with the vast AWS ecosystem for any other functionality you need.
- Compliance and Enterprise Use: Cognito is an AWS service, so it inherits AWS’s compliance certifications, fine-grained IAM controls, VPC endpoint support, etc., which might be important for enterprise or regulated environments. Firebase is more geared towards consumer app development and while it’s secure, enterprises might prefer the control AWS provides. Also, for enterprise scenarios requiring SSO with corporate directories, Cognito is equipped for that (with SAML/OIDC federation), whereas Firebase would fall short unless you use a different Google Cloud product.
In summary, Amazon Cognito vs Firebase is not about one being strictly better than the other, but about fit for context. If your application’s infrastructure is AWS-centric, you need tight security controls or SSO with enterprise providers, and you like the idea of integrating identity with AWS resources, Cognito is the natural choice. If you are building a mobile or web app rapidly, especially if using many of Firebase’s services, and want a developer-friendly package with generous free usage and you don’t need advanced enterprise features, Firebase Authentication could be a great choice. Many developers note that Firebase is simpler to get started, whereas Cognito can handle more complex use cases. One could even use Firebase for auth and AWS for other things, but you’d lose out on the easy AWS resource integration Cognito offers. Finally, nothing stops you from using both in some fashion (though that would be unusual) or migrating from one to the other if needs change – but migrating users between systems can be non-trivial (Cognito, for instance, won’t let you export passwords easily, by design, which is a security pro and a migration con ). So it’s worth evaluating these factors early on based on your project’s needs.
Pros and Cons of Amazon Cognito
Like any technology, Amazon Cognito comes with its advantages and disadvantages. Here’s a balanced look at the pros and cons:
Pros:
- Fully Managed and Scalable: Cognito can effortlessly handle millions of users and billions of authentication requests . You don’t have to worry about building a user backend or scaling it – AWS manages the heavy lifting, security, and reliability (Cognito processes over 100 billion authentications per month ). This makes it ideal for applications expecting growth, as you won’t need to re-architect your auth system.
- Rich Feature Set (CIAM): It provides comprehensive user identity features: self-service registration, account confirmation, password resets, multi-factor auth, social logins, enterprise SSO, groups/roles, profile attribute management, and more. Few services give both consumer-focused social login and enterprise SAML support in one package. Plus, features like Lambda triggers allow customizing workflows (for example, adding custom validations, auto-populating attributes, etc.) which adds to its flexibility.
- Seamless AWS Integration: This is perhaps Cognito’s biggest selling point. It integrates with AWS IAM, allowing you to map users to IAM roles for accessing AWS services . If your app uses AWS resources (S3, API Gateway, DynamoDB, etc.), Cognito provides a secure way for your users to directly access those resources without embedding secret keys. This is a unique advantage that competitor auth services don’t offer. Additionally, being an AWS service means you can monitor it with CloudWatch, manage it with Infrastructure as Code (CloudFormation/Terraform support for Cognito), and trust AWS’s security measures.
- Security and Compliance: Cognito offers high security out-of-the-box – user passwords are never stored in plain text (it uses strong hashing internally), it supports TLS encryption for all data in transit, and you can enable advanced security features (like compromised password detection, adaptive MFA) for additional protection . It also integrates with AWS CloudTrail for auditing. AWS maintains compliance for Cognito under programs like HIPAA, GDPR, etc., which can help your application meet regulatory requirements.
- Cost-Effective: As discussed, Cognito’s pricing is very attractive for large user bases. The free tier of up to 50k MAUs is a huge plus for startups. Even beyond that, the per-user cost is low, especially compared to enterprise identity providers. For B2C scenarios with lots of users, Cognito can be orders of magnitude cheaper than services like Auth0, Okta, etc., which often charge per active user at much higher rates . Essentially, you get a lot of value for a low cost.
- Multiple Language/Platform Support: AWS provides Cognito SDK support for many platforms (Java, Python, JavaScript/TypeScript, .NET, iOS, Android, etc.) and there’s the Amplify framework which simplifies using Cognito in web and mobile apps. This means whatever your tech stack, you can integrate Cognito without too much hassle. Also, the Hosted UI means you can get started without even writing the UI for login if you choose – Cognito can present a generic but functional login page for you.
Cons:
- Initial Learning Curve and Complex Configuration: Cognito has a reputation for not being the easiest service to grasp initially. Concepts like user pools vs identity pools, configuring App clients, callbacks, domain, IAM roles for identity pools – these can overwhelm newcomers. The AWS console wizard helps, but you still need to understand what’s happening to effectively use it. Documentation gaps have been noted; although AWS documentation is extensive, it sometimes lacks in tutorial-style guidance or clarity for certain advanced configurations . Developers often resort to community blogs or forums to figure out things (for example, setting up SAML federation or advanced triggers) because the official docs can be sparse on those topics.
- Developer Experience and Tooling: Tied to the above, some have found the developer experience with Cognito to be less smooth compared to competing solutions. For instance, the Hosted UI customization is limited – you can add a logo and CSS, but if you want a fully custom login page you’ll likely end up creating your own and using the Cognito SDK, which is extra work. The error messages or debugging info from Cognito can sometimes be less than clear (like generic “Not Authorized” errors). In contrast, something like Firebase might feel simpler with its tightly integrated console and usage examples. AWS is more geared toward flexibility and integration into larger systems, which can make the simple cases feel a bit complex.
- Vendor Lock-In / Migration Challenges: Once you have a large user base in Cognito, moving away can be challenging. Cognito does not allow exporting user passwords (for good security reasons). If you needed to migrate to another auth system, you would likely have to ask users to reset passwords or use the trick of a migration Lambda during sign-in (which requires maintaining the old system in parallel for a while). Similarly, if you rely on Cognito-specific features (like identity pools for AWS access), you’d have to re-engineer that with another solution. While this is true of many managed auth services, it’s worth noting that Cognito’s migration path is not trivial if you ever outgrow it or need to integrate with a different system.
- Some Feature Gaps and Quirks: Cognito is powerful but not perfect. For example, it doesn’t provide built-in support for certain OAuth2 flows like client credentials (for machine-to-machine you’d use a workaround or a different service), it currently doesn’t support refresh token rotation (a security best practice) although it does allow manual revocation. The password recovery via email/SMS flows are somewhat rigid in how you customize messaging. The UI for account management is minimal (no user profile editing widget out of the box; you have to build that using the SDK). Another quirk: some integrations (like linking a user’s multiple logins) can be finicky – developers have encountered odd issues linking social logins to an existing user, requiring extra handling in code . Also, user pools are region-specific; if you need a global user directory with data residency in multiple regions, you’d need to deploy multiple user pools and somehow sync or segment users, as Cognito doesn’t have a cross-region replication for user pools (aside from backing them up via import/export).
- Service Limitations: Cognito has certain limits (which can often be increased by AWS support if needed, but are there by default) – e.g., by default user pools allow up to 50,000 users without a limit increase (though that’s easily raised), up to 25 app clients per user pool, etc. These likely won’t affect most apps, but very large-scale or multi-tenant deployments might need to plan around them (for example, if you wanted to have a separate user pool per tenant and you have hundreds of tenants, that might get cumbersome or hit account limits).
- Latency Consideration: Because Cognito is a managed service in a specific AWS region, if your app’s users are globally distributed, those far from the region might have slightly higher latency on authentication calls (login, token refresh). This is usually only a few hundred milliseconds at worst, and not a deal-breaker (plus JWT verification is local once they have the token), but it’s something that some global apps consider – the workaround could be deploying Cognito in multiple regions and routing users, but that adds complexity (and there’s no built-in multi-region active-active support). Competing services like Firebase use Google’s global edge network for some things, potentially giving them a slight edge on distributed performance.
Amazon Cognito is a robust and cost-effective identity solution within AWS, with standout features for AWS resource integration and security. Its downsides are mostly around usability and certain limitations which AWS is continuously improving. Organizations that invest the time to understand Cognito’s model often find it extremely powerful. However, if someone is looking for a plug-and-play solution with ultra-simplified setup and doesn’t need the AWS tie-in, they might perceive Cognito’s complexity as a hurdle. Weighing these pros and cons in the context of your project’s requirements (scale, security, integration, budget, team expertise) will help determine if Cognito is the right choice. In many cases, the pros – especially being part of the AWS ecosystem – outweigh the cons, making Cognito a solid choice for implementing modern authentication and user management.
Conclusion
Amazon Cognito is a comprehensive platform for managing user identities, authentication flows, and authorization to AWS resources. We’ve seen how it provides a secure user directory with Cognito User Pools, a federation and AWS credential broker with Identity Pools, and numerous features like MFA, social and SAML logins, user groups/roles, and more – all while scaling to millions of users and integrating tightly with other AWS services. By following the tutorial and best practices, developers can implement a production-grade authentication system in their applications with relatively little code, offloading the heavy lifting of security and scale to AWS.
In a comparison of modern authentication solutions, Cognito stands out for its breadth of capabilities and cost efficiency, particularly for AWS-centric projects. While it may have a learning curve and certain quirks, the payoff is a highly customizable and powerful identity management system that can meet both simple and advanced use cases. From allowing quick social logins on a mobile app, to enforcing enterprise-grade security and compliance, Cognito covers a broad spectrum under one service.
In short, Amazon Cognito lets you “build securely, at scale”: you can focus on your application’s functionality and user experience, knowing that Cognito is handling the sign-up, sign-in, and safeguarding of your user accounts. With the knowledge of its working, components, and integration approaches as discussed, you should be well-equipped to utilize AWS Cognito effectively in your next project. Happy authenticating with Cognito!
Optimize Your Cloud Costs with Cloudchipr
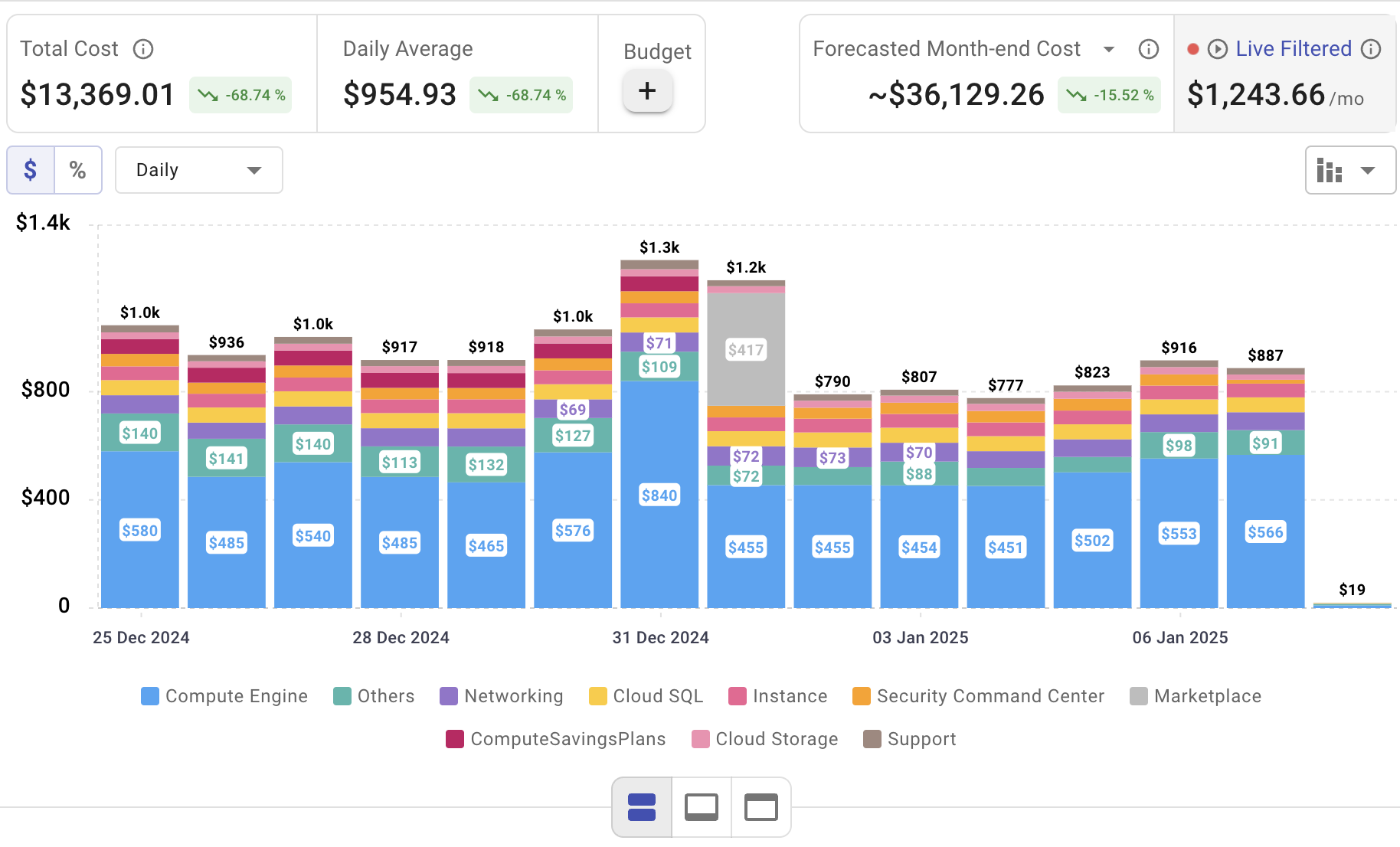
While Amazon Cognito streamlines user authentication and access management, keeping your cloud spend in check is equally crucial for long-term success. Cloudchipr empowers you to oversee and optimize costs across AWS, Azure, and GCP—all through a single, user-friendly platform. By combining Cognito’s robust identity controls with Cloudchipr’s proactive cost management, you can maintain a secure, budget-friendly environment that supports both operational efficiency and compliance.
Key Features of Cloudchipr
Automated Resource Management:
Easily identify and eliminate idle or underused resources with no-code automation workflows. This ensures you minimize unnecessary spending while keeping your cloud environment efficient.
Receive actionable, data-backed advice on the best instance sizes, storage setups, and compute resources. This enables you to achieve optimal performance without exceeding your budget.
Keep track of your Reserved Instances and Savings Plans to maximize their use.
Monitor real-time usage and performance metrics across AWS, Azure, and GCP. Quickly identify inefficiencies and make proactive adjustments, enhancing your infrastructure.
Take advantage of Cloudchipr’s on-demand, certified DevOps team that eliminates the hiring hassles and off-boarding worries. This service provides accelerated Day 1 setup through infrastructure as code, automated deployment pipelines, and robust monitoring. On Day 2, it ensures continuous operation with 24/7 support, proactive incident management, and tailored solutions to suit your organization’s unique needs. Integrating this service means you get the expertise needed to optimize not only your cloud costs but also your overall operational agility and resilience.
Experience the advantages of integrated multi-cloud management and proactive cost optimization by signing up for a 14-day free trial today, no hidden charges, no commitments.

.png)
.png)
.png)