AWS WAF: Understanding Amazon’s Web Application Firewall
.png)
Introduction
Every public-facing application attracts more than customers—it attracts bots, scanners, and exploit attempts the moment it goes live. Network firewalls stop at Layer 4, so you need a Layer 7 shield: AWS WAF. In just one service you get customizable rules, ready-made managed rules, granular rate limiting, detailed logs, and even bot control—all billed pay-as-you-go. This post explains what AWS WAF is, how it differs from AWS Shield and AWS Network Firewall, where it fits against providers like Cloudflare, and how to keep AWS WAF pricing sane.
What is AWS WAF?
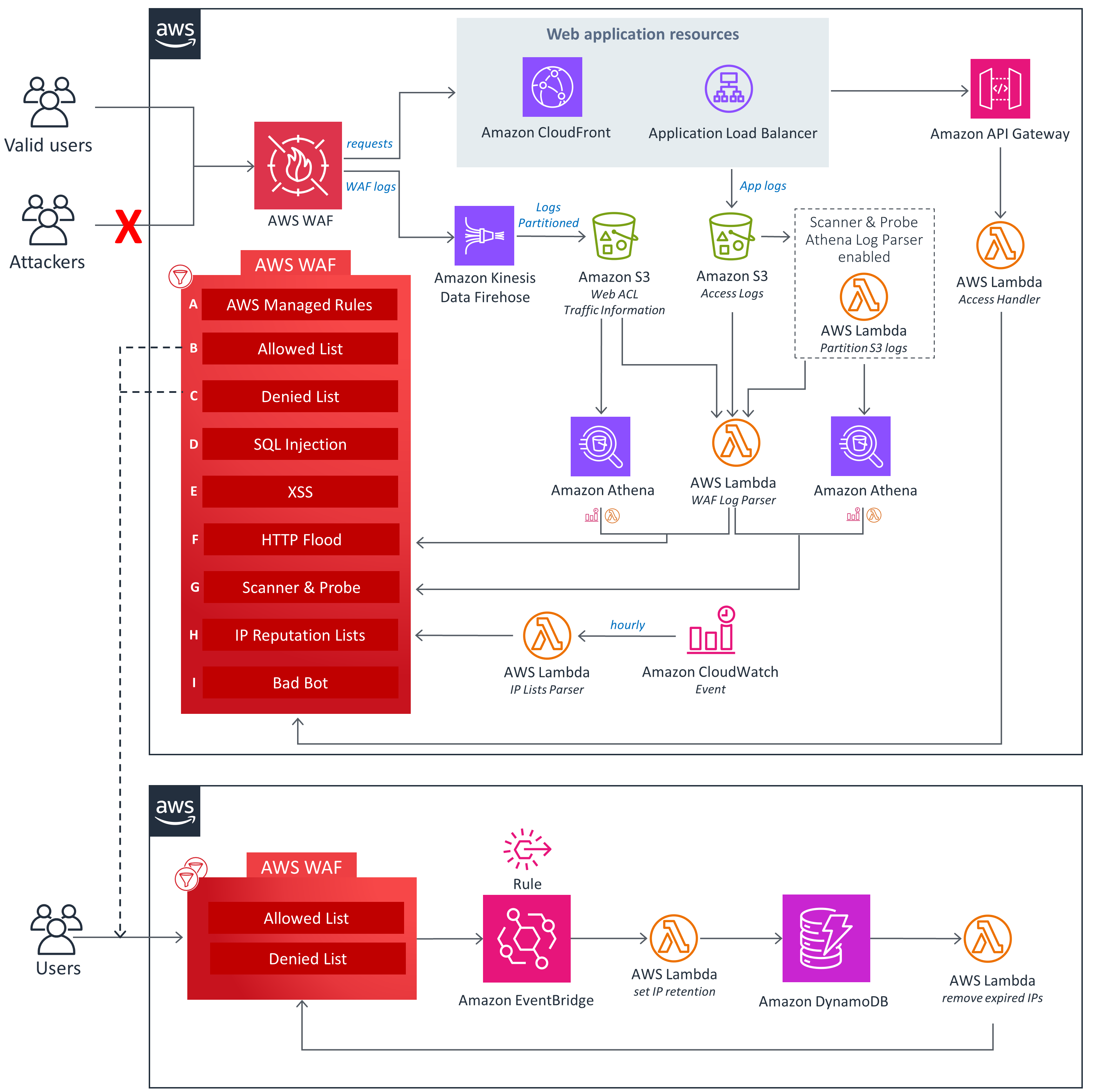
Amazon Web Services Web Application Firewall (AWS WAF) is a cloud-native security service that monitors and filters HTTP and HTTPS requests to your web applications and APIs. It sits in front of AWS resources (such as Amazon CloudFront distributions, Application Load Balancers, API Gateway REST APIs, AppSync GraphQL APIs, Cognito user pools, App Runner services, AWS Verified Access instances, and Amplify apps ) and enforces access control based on customizable rules. In practical terms, AWS WAF lets you specify conditions on incoming web traffic (like IP address, HTTP header values, URI paths, query strings, or known attack signatures) and then allow, block, or count requests that match those conditions. For example, an AWS-hosted e-commerce site might use AWS WAF to block requests that contain SQL injection patterns or known malicious user agents, while allowing normal user traffic. By default, a Web ACL (Access Control List) in AWS WAF either allows or blocks all requests, but you can attach custom rules so that specific unwanted traffic is filtered out. (Unmatched requests fall through to the Web ACL’s default action.)
At its core, AWS WAF operates by having you define a Web ACL and add rules to it . You then associate that Web ACL with one or more AWS resources. All incoming HTTP(S) requests to those resources are sent to AWS WAF for inspection. Each rule in the Web ACL examines request components (like IP, headers, body, etc.) and decides to allow, block, count, or challenge the request. If a rule matches, WAF performs the specified action (for example, blocking an SQL injection attempt). If no rules match, WAF applies the Web ACL’s default action (allow or block). In this way, AWS WAF provides a flexible, programmatic firewall at Layer 7 (the application layer), giving fine-grained control over web traffic for your applications.
How AWS WAF Works
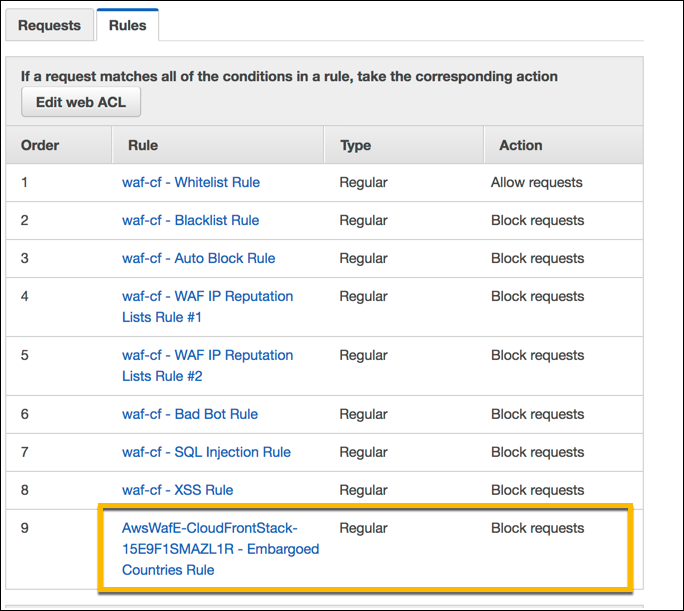
AWS WAF is organized around a few key concepts: Web ACLs, Rules, Rule Groups, and Actions. A Web ACL is an AWS resource that you create for a set of applications. It contains a list of rules (and rule groups) and specifies a default action (allow or block) for unmatched requests. You attach (associate) the Web ACL to AWS resources (like a CloudFront distribution or ALB) that you want to protect; thereafter, all incoming requests to those resources are evaluated against the Web ACL. Inside a Web ACL, Rules define how to inspect requests. Each rule has a statement that contains criteria (e.g. “IP matches this list” or “body contains this pattern”) and an action (Allow, Block, Count, or CAPTCHA/Challenge) to apply when a request meets the criteria. Rules can be simple (single criteria) or complex (combining multiple criteria with logical AND/OR/NOT). For example, you might create a rule that blocks requests where the source IP is in a blacklist AND the User-Agent header contains “BadBot”.
Rules can be organized into Rule Groups for reusability. AWS provides many AWS Managed Rule Groups (and you can also define your own) that bundle together multiple rules for common threats. You can add an AWS Managed Rules rule group to your Web ACL with a single setting. When you include a rule group in a Web ACL, AWS WAF runs every rule in the group against incoming requests. For example, AWS’s Bot Control managed rule group (discussed below) can be added to any Web ACL to automatically classify and throttle bot traffic.
AWS WAF processes incoming requests in a priority order: it evaluates rules one by one and takes the first matching action. If no rule matches, the Web ACL’s default action applies. When a rule is matched, AWS WAF can block the request (return HTTP 403 or custom response), allow it (pass it through), count it (just log the match but take no blocking action), or challenge it (serve a CAPTCHA or browser challenge). For instance, you might set a rule to block requests containing SQL injection patterns, or count requests from a suspicious IP range without blocking them, so you can monitor before enforcing a block. You can also set a default Web ACL action of either allow-all or block-all, depending on whether you follow an “allowlist” or “denylist” approach. All of this is managed through the AWS WAF console or APIs.
Key Components of AWS WAF
- Web ACLs: The top-level container for your WAF rules. An AWS resource’s web traffic is protected by one Web ACL. Each Web ACL has a default action (allow or block) for unmatched requests. You can attach one Web ACL to multiple resources (across same or different AWS accounts, if using Firewall Manager).
- Rules: Inspections you define inside the Web ACL. Each rule has a name, a statement of match criteria (IP match, string match, SQLi match, etc.), and an action (allow, block, count, or CAPTCHA). Rules are not standalone resources – they live inside a Web ACL or Rule Group.
- Rule Groups: Reusable sets of rules. AWS offers many AWS Managed Rules as pre-built rule groups (for OWASP Top 10, common bots, etc.), and you can also create your own rule groups. You add a rule group to a Web ACL much like adding a rule; AWS WAF then evaluates all rules in the group. (Managed rule groups from AWS and the AWS Marketplace are simply rule groups that AWS maintains.)
- Web ACL Capacity Units (WCUs): AWS WAF charges and limits are based on WCUs, which quantify the resource cost of your rules. Complex rules and large rule sets consume more WCUs. A Web ACL has a default allocation of 1500 WCUs; using more incurs additional charges.
AWS WAF’s internal processing flow is: resource gets a request → request is forwarded to WAF → WAF evaluates the Web ACL’s rules in order → applies the action of the first matching rule (or default action) → returns allow/block/response to the resource. This is conceptually similar to a traditional web application firewall, but it is fully managed, scalable, and integrated with AWS services. Because AWS WAF is invoked on Layer 7, it can see full HTTP(S) requests and thus block or inspect things like headers, query strings, cookies, or JSON bodies.
AWS WAF Rules and Managed Rules
A central feature of AWS WAF is its rule language for inspecting requests. AWS WAF rules let you search for a wide range of patterns and attributes in web requests. For example, you can write rules to detect:
- SQL injection or cross-site scripting (XSS): AWS WAF has built-in rule types that can scan parts of requests (headers, query strings, body) for signatures of SQL injection or malicious scripts. This blocks a common attack where someone tries to inject SQL or JavaScript into your pages.
- IP or geolocation filters: You can specify lists of IP addresses (CIDRs) to allow or block. You can also restrict by country. For instance, if you only do business in North America, you might block requests from other countries.
- HTTP parameters: You can match on strings or regexes in various request components (headers like User-Agent, URI paths, query parameters). For example, blocking requests where the User-Agent contains “BadBot” or Referer contains malicious content.
- Size and format checks: You can block requests based on the length of a header or the size of the request body, preventing overly large payloads.
- Rate-based rules: AWS WAF supports a special “rate-based” rule statement . This counts requests from an IP (or other key) over a 5-minute window and, if they exceed a threshold, can block or challenge them. This is useful for limiting flooding or brute-force attempts from a single source. (By default it aggregates by source IP, but you can scope it by other keys like headers or cookies to limit different kinds of traffic surge .)
- Combining conditions: Rules can include logical nesting (AND, OR, NOT) . For instance, you might block if both the IP is on a list AND the request contains certain bad content.
Each rule has an action when a match occurs. The basic actions are Allow, Block, or Count (just record it). AWS WAF also supports CAPTCHA/Challenge actions: you can require clients to solve a CAPTCHA or complete a challenge to prove they are human. This is useful against bots – you can add a CAPTCHA rule so that suspicious clients must solve it before proceeding. (CAPTCHA/challenge attempts may incur additional per-use charges, according to AWS WAF pricing.)
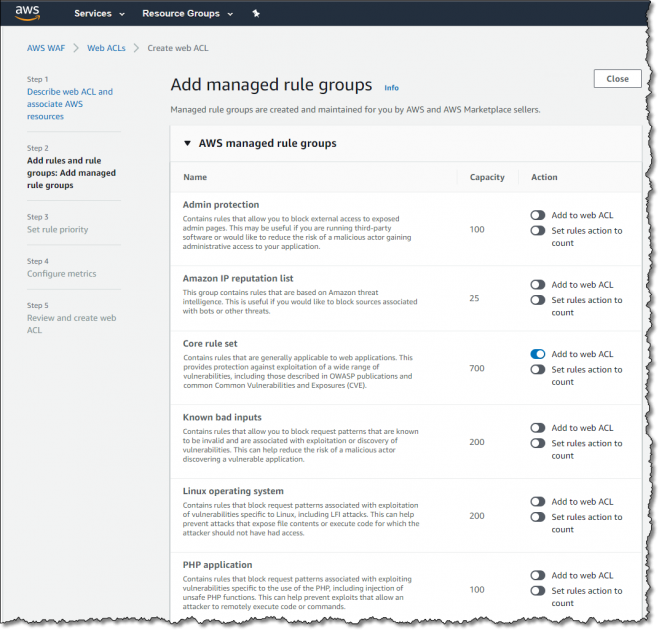
Besides custom rules you write yourself, AWS WAF offers AWS Managed Rules: AWS-maintained, pre-configured rule groups for common threats. Examples include rule groups for OWASP Top 10 vulnerabilities, Linux/Windows exploitation, SQLi/XSS common patterns, etc. These rule groups can be dropped into your Web ACL to provide immediate protection against known issues. There are also marketplace rule groups from AWS Partners. Using an AWS Managed Rule group simply costs a $1 per month subscription (pro-rated hourly) for each group added.
Rate Limiting with AWS WAF

AWS WAF provides powerful rate limiting through rate-based rules. A rate-based rule counts incoming requests in real time and can automatically block or otherwise act on clients that exceed a specified threshold . For instance, you could configure a rule to block any IP address that makes more than 1,000 requests in 5 minutes. Behind the scenes, AWS WAF groups requests by a key (by default the client IP) and tracks the count. When the count for that IP exceeds the limit, the rule triggers and takes the chosen action.
Rate-based rules are an effective tool for DDoS and flood protection. In an e-commerce scenario, for example, a spike of malicious traffic from a botnet could be curtailed by rate limiting, protecting the origin servers from overload . By default, rate-based rules aggregate by source IP, but AWS WAF also lets you use other dimensions (like headers, cookies, or URL paths) as the aggregation key . This flexibility means you could limit requests per user session or per API endpoint, not just per IP. Once the threshold is breached, you can choose to block further requests or trigger a CAPTCHA challenge on that source. AWS provides detailed examples (e.g. limiting login attempts or API calls) in its documentation.
AWS WAF Bot Control

A standout feature of AWS WAF is the Bot Control managed rule group . This is a specialized AWS Managed Rules group that identifies and manages bot traffic. With Bot Control, you can automatically monitor, block, or rate-limit known bots and even detect unknown or malicious bots. It classifies bots such as scrapers, crawlers, status monitors, or search engine bots. For example, if you run an online storefront, a web scraper may try to harvest your product data; AWS WAF Bot Control can recognize many such scrapers and either label them or block them.
Bot Control offers two protection levels. The “common” level adds labels to requests from self-identifying bots (e.g. Googlebot) and applies some basic heuristics. The “targeted” (advanced) level uses more sophisticated techniques like browser challenges, fingerprinting, and optional machine-learning to find stealthy or malicious bots that try to disguise themselves . You can add the Bot Control rule group to your Web ACL to automatically enrich your logs and metrics with bot categories. For instance, Bot Control inserts labels into CloudWatch metrics and AWS WAF logs identifying a request as coming from, say, a known “Googlebot” or a “high-confidence bad bot”. You can then write additional WAF rules that match on these labels to block or throttle that traffic.
The Bot Control feature includes a dashboard (in the WAF console) that shows what percentage of your traffic is bots, what types of bots, etc. Note that AWS WAF Bot Control is a paid managed rule group: you get the first 10 million requests per month (common bots) and 1 million (targeted bots) for free, after which standard request charges apply . AWS recommends using Bot Control in conjunction with your own rules – for example, if a request is flagged as “bad bot” by Bot Control, you might send a 403 or a rate limit. According to AWS documentation, you can also integrate Bot Control with AWS Firewall Manager to deploy it across multiple accounts.
Logging and Monitoring
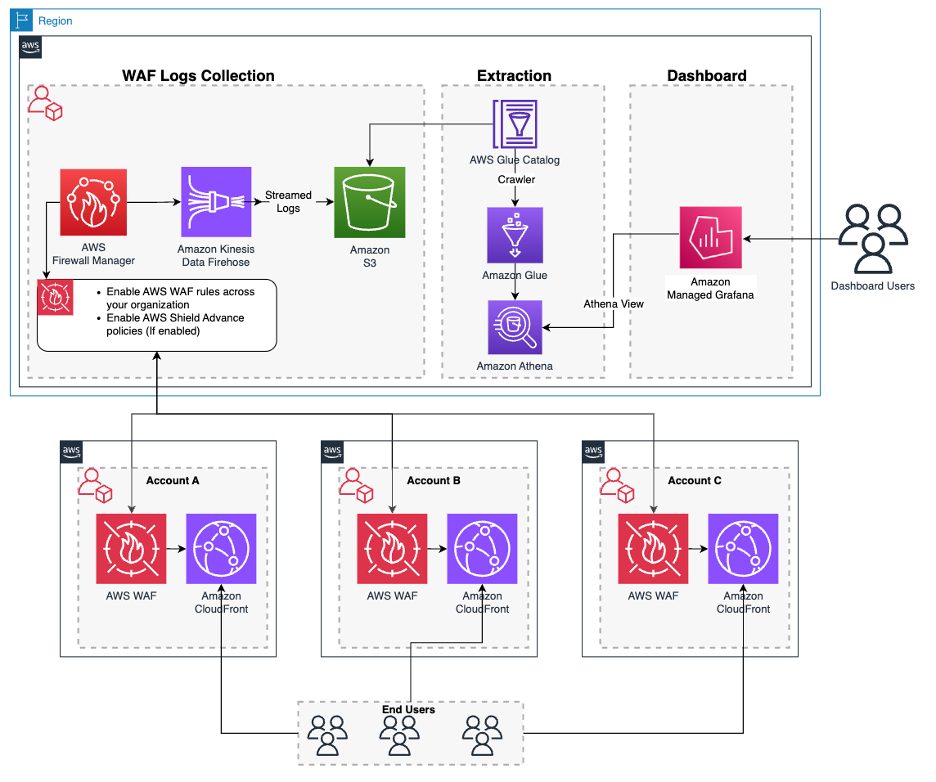
Visibility is a key part of WAF protection. AWS WAF can generate detailed logs of all web traffic evaluated by a Web ACL. When you enable logging for a Web ACL, every request (or a sampled subset) that reaches the WAF is recorded, including the time, request data, and which rules (if any) were matched . These logs can be sent to Amazon CloudWatch Logs, an Amazon S3 bucket, or Amazon Kinesis Data Firehose for analysis . For example, the logs include HTTP methods, headers, URI, body snippets (if logging bodies), plus which rule or rule group blocked or allowed the request. This information is invaluable for incident investigation, analytics, and compliance auditing. (For instance, a healthcare application under HIPAA compliance could archive WAF logs to audit all attempts to access sensitive data.)
Because logging can generate a high volume of data, AWS charges separately for log delivery based on the destination . You will incur the normal AWS WAF charges plus whatever the log delivery service costs (CloudWatch Logs, S3 storage, or Kinesis fees) . In practice, many teams start with CloudWatch Logs because it integrates easily with CloudWatch Insights for quick querying. Whether you use CloudWatch or S3, the recorded fields and format are documented by AWS, and you can filter logs on specific criteria (e.g. only log blocked requests, or only log requests that matched certain rules). In short, AWS WAF logs give you a full audit trail of web requests and WAF decisions, which is critical for both debugging security rules and meeting regulatory needs.
Comparing AWS WAF with Other Solutions
AWS provides multiple security tools, and it’s important to distinguish AWS WAF from them and from third-party services:
- AWS Shield (vs WAF): AWS Shield is AWS’s DDoS protection service. Shield Standard is automatically included at no extra cost for all AWS customers and protects against most common L3/L4 network DDoS attacks (for example, TCP SYN floods or UDP reflection attacks on CloudFront or Route 53) . Shield Advanced (paid) provides enhanced DDoS mitigation, covering additional resources (ALBs, EC2, etc.) and also offering advanced analytics and 24/7 support. In contrast, AWS WAF operates at the application layer (L7). While WAF can also mitigate application-layer DDoS (for example, by blocking bad HTTP floods or using rate-based rules), its primary purpose is inspecting and filtering web requests rather than volumetric attacks. In practice, you often use them together: AWS WAF for layer-7 filtering (SQL injection, bot control, etc.), and AWS Shield to absorb or scrub large-scale L3/4 attacks. The AWS documentation explicitly states that you can use WAF Web ACLs to help minimize DDoS effects, but AWS Shield provides dedicated DDoS defense for AWS resources. Shield Advanced also offers application-layer DDoS mitigation, but unlike WAF it’s billed as a subscription service (not pay-per-request).
- AWS Network Firewall (vs WAF): AWS Network Firewall is a VPC-level network firewall. It is designed to protect traffic at the network layer (L3/L4) within your VPCs, using stateful packet inspection rules (often defined with Suricata rule syntax). According to AWS, Network Firewall provides fine-grained control over network traffic across VPC subnets . In other words, if you want to filter arbitrary IP traffic (HTTP and non-HTTP, ingress and egress) across your AWS network, you would use Network Firewall. In contrast, AWS WAF is specifically for HTTP(S) web traffic going to AWS services (CloudFront, ALB, API Gateway, etc.) . So they operate at different layers: Network Firewall inspects raw network packets (can block a port, a protocol, or detect malware signatures in any protocol), whereas WAF inspects HTTP requests and understands web semantics (cookies, JSON, script content, etc.). In many architectures, you might use both: Network Firewall to protect the VPC perimeter (e.g. block IPs at the subnet level) and WAF to protect application endpoints.
- AWS WAF vs Cloudflare WAF: Cloudflare is a popular third-party CDN and security provider that also offers a WAF as part of its service. Cloudflare’s WAF is delivered via their global edge network (requests pass through Cloudflare’s proxy), whereas AWS WAF is used on traffic to your AWS resources (or any origin behind CloudFront). A few high-level differences: Cloudflare provides built-in CDN caching, DNS, and global load balancing along with its WAF, as a combined SaaS offering. AWS WAF is part of your AWS cloud deployment; it integrates natively with AWS infrastructure but doesn’t by itself cache or route traffic. In terms of functionality, both offer rule-based filtering, bot management, and managed rulesets. The pricing and administrative models differ: Cloudflare’s WAF is typically included in subscription tiers, whereas AWS WAF is pay-as-you-go based on usage. Ultimately, the choice depends on your architecture: if you are running entirely within AWS, using AWS WAF makes sense. If you want a vendor-neutral, multi-cloud or on-prem proxy solution, something like Cloudflare’s WAF may be appropriate. The key point is that AWS WAF is focused on protecting AWS-hosted applications, while Cloudflare is an external edge service.
AWS WAF Pricing and Cost Management
Understanding AWS WAF’s pricing is important for budgeting and for writing cost-effective rules. AWS WAF pricing is usage-based. You pay for:
- Web ACLs and Rules: There is a monthly fee (prorated hourly) for each Web ACL you create, and for each rule you add to a Web ACL. Effectively, every Web ACL costs a fixed price, and every rule you put in it also costs (at current rates around $1 per rule per month, but always check the current price page).
- Requests: You pay per million requests processed by your Web ACL. AWS provides a default allowance of 1500 WCUs at no extra charge; once your Web ACL processes traffic requiring more than 1500 WCUs (for example, many rules or large request bodies), additional usage is charged (for instance, $0.20 per million requests for each extra 500 WCUs beyond 1500). Similarly, inspecting request bodies beyond a default size (16 KB) incurs a small per-request fee.
- Rule Groups: If you add any rule groups (custom or managed) to your Web ACL, each rule group incurs a $1 per month fee. This includes AWS Managed Rule groups and ones from the AWS Marketplace. For example, adding the Bot Control rule group costs an extra $1/month (independent of traffic).
- Bot Control or Fraud Control: Some advanced managed features have separate pricing. AWS WAF Bot Control (the managed rule group) grants you the first 10 million common bot detections and 1 million targeted bot detections free each month; beyond that, normal request fees apply. Similarly, the Account Takeover Prevention (ATP) and Fraud Control rule groups have their own pricing (e.g. a $10/month subscription plus a per-request fee).
- CAPTCHA/Challenge: Using CAPTCHA or challenge actions incurs a cost per challenge attempt or response, as listed in the pricing table (because those engage AWS’s challenge infrastructure).
In practice, a simple small Web ACL might cost just a few dollars per month plus a few cents per million requests. A more complex one with many rules or high traffic will cost more. AWS provides a WAF pricing page and a pricing calculator to help estimate.
Because WAF costs can rise with complex rules or high traffic, AWS and the community recommend cost-management strategies. Some of the best practices include:
- Limit scope of expensive rules: If you use advanced AWS Managed Rules (like Bot Control, or ATP), use scope-down statements or early allow rules to exclude obvious traffic first . For example, only run the Account Takeover Prevention (ATP) rules on your login URL, not on every page of your site. You can do this by adding a scope-down condition to the managed rule statement, or by placing other rules earlier in the ACL to filter out irrelevant traffic.
- Order your rules efficiently: Place lightweight, broad rules before more expensive ones. For instance, block known bad IPs or patterns first, and apply machine-learning based rules (which cost more) later. AWS specifically suggests ordering Bot Control, then ATP, then ACFP if using multiple managed rule groups to minimize cost impact.
- Use count mode and testing: Before enforcing a new rule, run it in “Count” mode against live traffic to see how many requests match . This helps avoid accidentally blocking legitimate users. Also deploy changes first in a staging environment and review the WAF logs (which show rule matches) before going to production.
- Stay under default WCU limits: A single Web ACL has 1500 free WCUs. If you approach that limit, you will incur additional request fees. You can manage this by using fewer or simpler rules, or by splitting rules into multiple Web ACLs if needed.
- Skip WAF on static content: If you have static-only endpoints (like a CloudFront distribution serving only S3 static content), you may not need a WAF at all. The AWS blog suggests not applying a Web ACL to truly static sites to save cost.
- Adjust challenges smartly: If using CAPTCHA or challenges, set reasonable immunity times (so that users who solved a CAPTCHA aren’t re-challenged too soon) and make sure to check for the aws-waf-token cookie if using challenges. AWS provides guidance on this to minimize unnecessary WAF processing and charges.
- Logging: Enable logging to monitor the effects of your rules, but remember logging itself can incur costs (especially if logging all requests). Often teams log only blocked requests or use sampling to balance visibility with cost.
Overall, good design and ongoing review are key: avoid too many broad rules, test configurations, and use the native CloudWatch metrics and logs for visibility. This aligns with AWS’s published best practices for efficient, cost-effective WAF deployments.
AWS WAF Best Practices
Building on the cost-management tips, here are some general best practices for working with AWS WAF:
- Follow the principle of least privilege: Only allow what your application really needs. For a public API, use an “allowlist” approach for expected URIs and patterns. For a private admin console, consider “deny all except these IPs.” By default, WAF allows all unless you block explicitly, so be thoughtful about default actions and rule coverage.
- Use AWS Managed Rules where appropriate: AWS provides pre-tested rule groups for common attacks and fraud. For example, the AWS-Managed OWASP Top 10 rule group covers many injection and cross-site scripting attacks. Using these can save time, but you should still test them (perhaps in count mode) before enabling all blocking.
- Regularly update and tune rules: Threats evolve, so periodically review WAF logs for new patterns. You might need to add new rules (or whitelist a safe but blocked request). AWS WAF makes it easy to update rules on the fly.
- Test before enabling: As AWS docs emphasize, always test new rules by using the Count action first and reviewing results . This way, you ensure you’re not disrupting normal users. After a satisfactory trial, switch to block/allow mode.
- Use labels for complex logic: AWS WAF supports labeling requests (e.g. from one rule to another) to build multi-stage logic. For example, you could label requests from a login page and then apply specialized rules only to labeled requests. Labels are also used by managed rules (like Bot Control) to identify bot categories.
- Integrate with AWS Security services: AWS WAF works with AWS Firewall Manager for multi-account management and with AWS Security Hub or GuardDuty for consolidated alerts. Enable WAF logs ingestion into AWS Security Lake or Splunk for broader security analysis.
- Plan for propagation delay: When you update WAF rules, it can take a few seconds to minutes to propagate globally. During this time, behavior might be inconsistent. AWS notes this in their docs . Generally, allow for a short propagation period after changes.
By following these guidelines – minimizing unnecessary rules, testing carefully, and monitoring – you can leverage AWS WAF as an effective part of your security posture. AWS’s own documentation and blogs emphasize efficiency and staged rollouts, and by doing so you’ll keep both your applications safer and your costs under control.
Conclusion
AWS WAF is a powerful, flexible web application firewall built for AWS workloads. It works by using Web ACLs and rules to inspect and act on web requests. Key features include custom rules for SQLi/XS S and IP filtering, AWS Managed Rules (including specialized protection like Bot Control), rate-based throttling of traffic, and comprehensive logging. When compared to AWS Shield (which focuses on DDoS at network layers) or Network Firewall (which handles general VPC traffic), AWS WAF is the go-to tool for HTTP(S) traffic filtering at the application layer. Its pricing model charges per Web ACL, rule, and request volume, so best practices emphasize efficiency: test rules first, scope them narrowly, and use AWS-managed protections judiciously. With these practices, teams can leverage AWS WAF to block threats, limit malicious traffic, and keep their web applications secure across industries.
Monitor Your AWS WAF Spend with Cloudchipr
Setting up AWS WAF is only the beginning—actively managing cloud spend is vital to maintaining budget control. Cloudchipr offers an intuitive platform that delivers multi‑cloud cost visibility, helping you eliminate waste and optimize resources across AWS, Azure, and GCP.
Key Features of Cloudchipr
Automated Resource Management:
Easily identify and eliminate idle or underused resources with no-code automation workflows. This ensures you minimize unnecessary spending while keeping your cloud environment efficient.
Receive actionable, data-backed advice on the best instance sizes, storage setups, and compute resources. This enables you to achieve optimal performance without exceeding your budget.
Keep track of your Reserved Instances and Savings Plans to maximize their use.
Monitor real-time usage and performance metrics across AWS, Azure, and GCP. Quickly identify inefficiencies and make proactive adjustments, enhancing your infrastructure.
Take advantage of Cloudchipr’s on-demand, certified DevOps team that eliminates the hiring hassles and off-boarding worries. This service provides accelerated Day 1 setup through infrastructure as code, automated deployment pipelines, and robust monitoring. On Day 2, it ensures continuous operation with 24/7 support, proactive incident management, and tailored solutions to suit your organization’s unique needs. Integrating this service means you get the expertise needed to optimize not only your cloud costs but also your overall operational agility and resilience.
Experience the advantages of integrated multi-cloud management and proactive cost optimization by signing up for a 14-day free trial today, no hidden charges, no commitments.

.png)
.png)
.png)