What Does a Cloud Engineer Do? A Practical Overview
.png)
Introduction
The cloud only feels simple when a cloud engineer makes it so. Networks are segmented, identities scoped, pipelines automated, and observability wired to what users feel. You ship faster without trading away security, reliability, or cost control. Let’s dive in to understand better.
What “Cloud Engineer” Actually Does
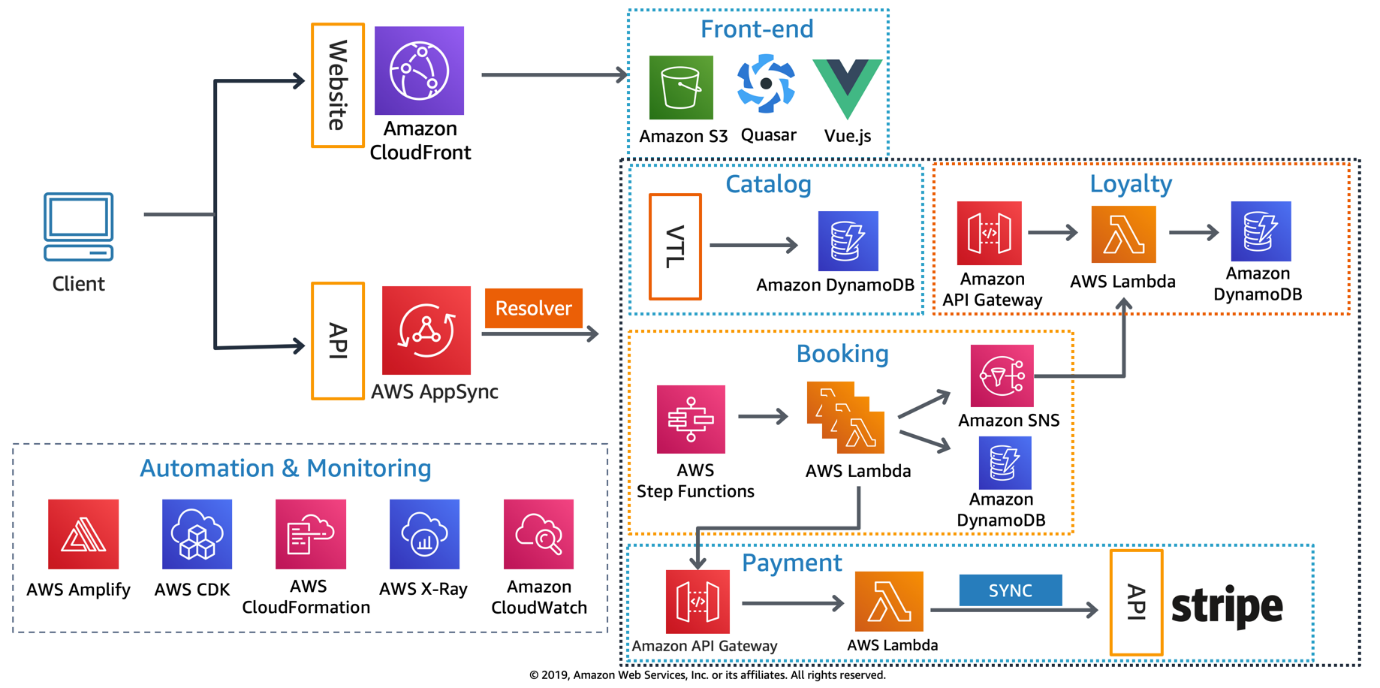
A cloud engineer designs and automates the building blocks of the cloud—compute, storage, networking, identity, observability, and security—on platforms like AWS, Azure, and Google Cloud. They turn architecture into code, wire up pipelines, and add guardrails so changes are safe, repeatable, and auditable. In practice, they connect teams and providers by provisioning resources, enforcing policy, and keeping systems reliable, secure, and cost-aware.
Core responsibilities include:
- Designing well-architected workloads using pillars such as reliability, security, cost optimization, performance, and sustainability.
- Automating infrastructure with Infrastructure as Code (IaC), CI/CD, and policy-as-code.
- Operating production systems with monitoring, logging, tracing, SLOs, capacity planning, and incident response.
- Implementing security controls aligned to frameworks like ISO/IEC 27017 and the CSA Cloud Controls Matrix (CCM).
- Optimizing spend through right-sizing, autoscaling, and demand shaping.
Opinion: The best cloud engineers think in systems, not services. They own the feedback loops between architecture, operations, security, and cost.
How It Differs From Related Roles
- Cloud architect vs cloud engineer. Architects own target state and guardrails; cloud engineers turn that design into running, observable, secure workloads and keep them healthy using Well-Architected principles.
- SRE vs Cloud Engineer. SRE treats operations as a software problem and formalizes reliability through SLOs, error budgets, and toil reduction. Many cloud engineers adopt SRE practices, but SRE is a distinct discipline with reliability commitments as its north star.
- DevOps engineer vs cloud engineer. “DevOps” is a culture and set of practices. A cloud devops engineer typically focuses on CI/CD, platform automation, and developer workflows on cloud, while a cloud engineer covers a broader infra remit including networking, identity, and multi-account governance.
- Cloud security engineer. Cloud security engineer. Specializes in IAM, data protection, threat detection, and compliance mapping to frameworks such as ISO/IEC 27001, ISO/IEC 27017, SOC 2, and CSA CCM; many organizations staff this as a dedicated role.
- Cloud support engineer. Focused on triage, customer advocacy, and escalation paths across provider services, adjacent to “computer support specialists” in BLS taxonomy.
Core Concepts

- Models. IaaS, PaaS, SaaS, and public, private, hybrid, multi-cloud; choose the least-managed option that still meets speed, control, and compliance needs.
- Identity boundaries. Tenants, accounts, subscriptions, and projects define blast radius; enforce least privilege with org policies, SCPs, or Azure Policy.
- Landing zone. Baseline networking, IAM, logging, encryption, and audit trails; include tagging, budgets, and break-glass access from day one.
- Networking. Plan CIDR, routing, and DNS up front; prefer private endpoints and controlled egress.
- Data. Set RPO/RTO, test restores, encrypt at rest and in transit, and manage keys responsibly.
- Reliability. Multi-AZ by default, SLOs for user experience, load and chaos tests to verify.
- Security. Least privilege, patch baselines, secret rotation, and detection with clear response paths.
- Observability. Metrics, logs, and traces tied to SLOs; alerts must be actionable and owned.
- Cost. Right-size, autoscale, use commitments where steady, track unit costs, and remove idle.
- Automation & governance. Everything through IaC and CI/CD; detect drift, apply policy-as-code, review access, and log changes.
Skills And Tools That Matter
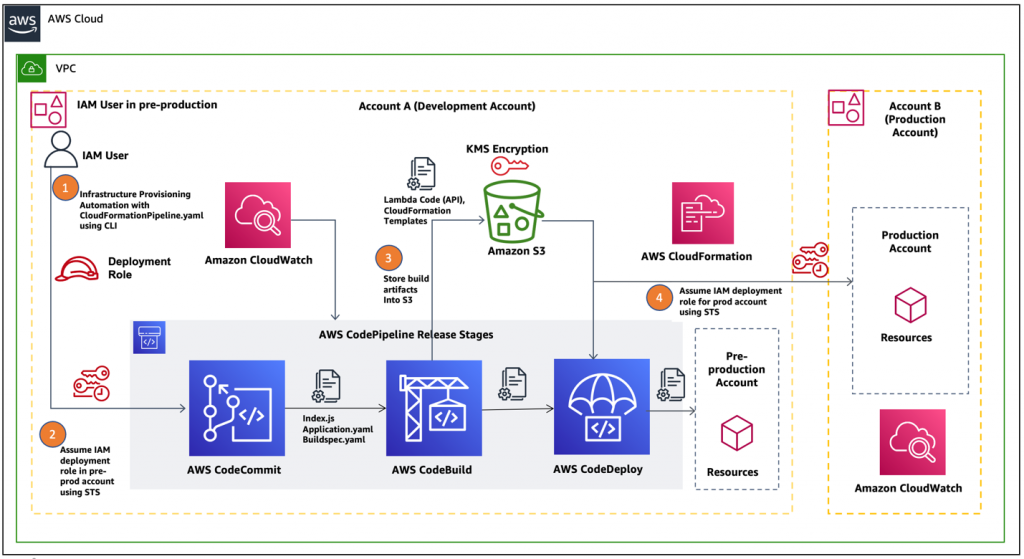
- IaC & automation. Terraform or Pulumi, CloudFormation or Bicep, reusable modules, drift detection, and policy checks in CI; strong Bash plus Python or Go, with provider CLIs baked into pipelines.
- CI/CD & releases. GitHub Actions, GitLab CI, or Azure DevOps; Argo CD or Flux for GitOps; blue-green or canary, artifact versioning, and quick rollbacks.
- Networking & identity. VPC/VNet design, subnetting, DNS, load balancers, private connectivity, IAM roles and policies, SSO and federation.
- Containers & runtimes. Docker/OCI, Kubernetes (EKS/AKS/GKE), autoscaling, node and pod hardening, and service mesh only when it earns its keep.
- Data & caching. Managed databases with backups and PITR, replication where needed, object storage lifecycle rules, Redis or Memcached for hot paths.
- Observability. Metrics, logs, and traces via OpenTelemetry, SLOs with error budgets, actionable alerts routed to owners, dashboards tied to user impact.
- Security. KMS with key rotation, secrets management, least privilege, image and dependency scanning, posture checks, and detection with clear response playbooks.
- Cost & capacity. Consistent tagging and budgets, anomaly detection, rightsizing and autoscaling, commitments for steady usage, unit economics tracked.
- Reliability & DR. Multi-AZ by default, multi-region when justified, health checks, chaos and failover tests, documented and tested RTO/RPO.
- Governance & policy. Org hierarchy, policy-as-code with OPA/Conftest or cloud-native policies, change approvals, audit trails, and periodic access reviews.
Certifications And Courses
Certifications don’t replace experience, but they give a shared vocabulary, a structured path, and proof you can work within provider guardrails. Use them to frame hands-on projects, not as an end goal.
Pick a path (and what each proves):
- Vendor-neutral foundations.
- CSA CCSK → cloud security concepts and shared responsibility.
- CompTIA Cloud+ → multi-cloud infrastructure basics, troubleshooting.
- Kubernetes platform.
- CNCF CKA/CKAD/CKS → cluster ops, app delivery, and hardened workloads.
- AWS track.
- Solutions Architect – Associate → core design patterns.
- SysOps Administrator → day-2 operations.
- DevOps Engineer – Professional or Security – Specialty → advanced automation or defense-in-depth.
- Azure track.
- AZ-104 Azure Administrator → identity, storage, network ops.
- AZ-305 Solutions Architect or AZ-500 Security Engineer → design or security depth.
- Google Cloud track.
- Associate Cloud Engineer → deploy and operate hands-on.
- Professional Cloud Architect or Security Engineer → design or security specialization.
- FinOps & cost.
- FinOps Certified Practitioner (FOCP) → cost allocation, forecasting, and optimization fundamentals.
How to make certs useful:
- Tie each exam to a deliverable: a small landing zone, a CI/CD pipeline, or a DR drill.
- Study from official provider learning paths, then lab your own implementations.
- Write IaC for everything you configure; commit it to a public repo with readme and runbooks.
- After passing, run a Well-Architected style review and fix one high-risk item per pillar.
What Does A Cloud Engineer Do Day-To-Day?
- Build and evolve landing zones and platform services.
- Write IaC, automate deployments, and enforce policies in CI/CD.
- Run Well-Architected or equivalent reviews and fix high-risk items.
- Define SLOs with product teams, tune alerts, and drive postmortems the SRE way.
- Implement and audit security controls against ISO/IEC 27017 and CSA CCM.
- Track spend, forecast, and remove waste, tying costs to value.
How To become A Cloud Engineer
- Ground yourself in fundamentals. Learn compute, storage, networking, Linux, containers, and Git. Skim NIST’s cloud models to anchor terminology.
- Pick a primary cloud. Choose AWS, Azure, or Google Cloud and stay there until you can build a small landing zone. Learn its Well-Architected pillars and native IAM.
- Automate everything. Use IaC (Terraform/Pulumi or native), CI/CD, and policy-as-code to make changes safe and repeatable. Add drift detection.
- Practice reliability early. Define one user-facing SLO, wire basic metrics, logs, and traces, and run a load test. Add a simple chaos test.
- Harden security by default. Enforce least privilege, manage secrets, enable KMS, and rotate keys. Add baseline detection and response runbooks.
- Cover data and recovery. Set RPO/RTO, enable backups with PITR, and test a restore. Use multi-AZ by default and document failover steps.
- Make costs visible. Tag resources, set budgets and alerts, right-size, and turn on autoscaling. Track a simple unit metric like cost per request.
- Ship a small service end-to-end. Containerize an app, deploy with IaC, expose it through a load balancer, add CI/CD, observability, and a rollback.
- Validate with one certification. Pick a single entry-level cert aligned to your chosen cloud and tie exam objectives to your project work.
- Show outcomes, not effort. Write short postmortems, list SLO improvements, and quantify cost reductions. Share lessons learned.
FAQ
- Q: What is a cloud engineer?
- A: A practitioner who designs, automates, and operates cloud workloads using provider best practices and neutral standards such as NIST’s cloud definition and reference architecture.
- Q: What does a cloud engineer do on a typical week?
- A: Implements IaC, runs Well-Architected reviews, tunes SLOs and alerts, patches and rotates keys, and removes cost waste while shipping features with teams.
- Q: How to become a cloud engineer without prior cloud experience?
- A: Learn NIST models, pick one cloud, complete an associate-level certification or CCSK, build a small but production-like project, and document reliability and cost outcomes.
- Q: What about cloud engineer salary?
- A: It varies by scope and title. Benchmarks from adjacent roles: software developers $133,080 median, information security analysts $124,910 median, network/system admins $96,800 median in August 2025.
- Q: Where do security frameworks fit?
- A: Use ISO/IEC 27017 for cloud security control guidance and map to CSA CCM for comprehensive coverage and shared responsibility alignment.

.png)
.png)
.png)