AWS VPC (Amazon Virtual Private Cloud) – A Comprehensive Beginner’s Guide
.png)
Introduction
Amazon Virtual Private Cloud (VPC) is the bedrock of AWS networking. If you’re new to the cloud, understanding what a VPC is—and how it shapes traffic—is essential. This guide starts from square one, explaining why a VPC matters, then walks through its core building blocks such as subnets, route tables, gateways, and endpoints. We’ll demystify VPC pricing—from free components to paid extras like interface endpoints—and illustrate these concepts with real-world examples from production environments. Along the way, you’ll pick up practical design tips, learn when to use VPC peering versus Transit Gateway, and explore advanced capabilities such as AWS VPC Lattice. Ready to dive in?
What Is VPC in AWS and Why It Matters

Amazon Virtual Private Cloud (VPC) is essentially your own isolated network environment within the AWS cloud. According to AWS documentation, a VPC allows you to launch AWS resources “in a logically isolated virtual network that you’ve defined,” resembling a traditional network in your data center while leveraging AWS’s scalable infrastructure. In simpler terms, a VPC is like having a private section of AWS where you control the networking – you decide the IP address range, subnet configuration, routing, and security. This isolation provides increased security and control, letting you design your cloud network to closely mirror an on-premises network architecture (with subnets, firewalls, etc.) but without needing to manage the physical hardware.
Why does a VPC matter? Because it defines the security and connectivity of everything you deploy in AWS. By default, resources in one VPC cannot communicate with those in another VPC or the internet unless you explicitly allow it. This isolation is a big advantage – it means you can host sensitive applications in the cloud with fine-grained control over who can access them. Every AWS account comes with a default VPC in each region to get you started quickly, so beginners can launch their first EC2 instances without configuring a network from scratch. However, understanding VPCs is important when you start designing production environments, because a well-designed VPC ensures your applications are secure, highly available, and scalable from the networking perspective.
In short, an AWS VPC is the cornerstone of cloud networking on AWS – it’s the container for your cloud infrastructure’s networking configuration. Let’s break down the key components that make up a VPC.
Key Components of an AWS VPC
An AWS VPC is composed of several core components that together form your virtual network. Here are the main components and concepts you should know:
CIDR Block (IP Address Range)

When you create a VPC, you assign it an IP address range in CIDR notation (e.g., 10.0.0.0/16). This range defines the pool of private IP addresses available for instances and subnets in the VPC. Plan this range carefully to avoid overlap with other networks (especially if you’ll connect multiple VPCs or connect to on-premises networks); AWS recommends using non-overlapping ranges for each VPC.
Subnets (Public and Private)

A subnet is a range of IP addresses within the VPC, carved out from the VPC’s CIDR block. Each subnet exists in a single Availability Zone (AZ). Subnets are typically categorized as public subnets (able to reach the internet) or private subnets (no direct internet access). For example, you might put web servers in a public subnet (so they can send/receive traffic from the internet), while placing databases or internal application servers in a private subnet for security. Using multiple AZs for your subnets is a best practice for high availability – if one AZ has an outage, resources in another AZ can still operate.
Route Tables

A route table contains routing rules that determine how traffic flows out of a subnet. Each subnet is associated with a route table. For instance, a route table for a public subnet will have a route that directs all outbound internet traffic (0.0.0.0/0) to the Internet Gateway, whereas a private subnet’s route table might direct 0.0.0.0/0 to a NAT gateway (see below). Essentially, route tables tell your subnet where to send traffic destined for elsewhere (another subnet, an internet gateway, a peering connection, etc.).
Internet Gateway (IGW)

An Internet Gateway is a horizontally scaled, redundant gateway that allows communication between your VPC and the public internet. Attaching an IGW to your VPC, and having a route to it in a subnet’s route table, will enable instances in that subnet to reach the internet (and vice versa, if those instances have public IPs). A subnet with a route to an IGW is often called a “public subnet”. The IGW is what gives your VPC a presence on the internet, but you control which subnets (and therefore which instances) are exposed.
NAT Gateway

Instances in private subnets (by definition, subnets without direct internet routing) often still need to access the internet outbound (for example, to download software updates or call external APIs). For this, AWS offers a NAT Gateway service. A NAT gateway is a managed Network Address Translation service that lives in a public subnet and allows private subnet instances to initiate outbound connections to the internet, while preventing inbound connections from the internet . Essentially, the NAT gateway forwards traffic from private instances out to the internet using the NAT gateway’s public IP address. This keeps your private instances securely hidden (they have no public IP), yet they aren’t cut off from necessary external communications. (Note: NAT gateways are billed hourly and per GB of data processed, which we’ll cover in the pricing section.)
Security Groups and NACLs

Security Groups and Network ACLs (Access Control Lists) are the primary network security layers in a VPC. A security group is essentially a virtual firewall for an instance (or ENI) that controls inbound and outbound traffic at the instance level. You can specify which ports and sources/destinations are allowed. Security groups are stateful (meaning response traffic is automatically allowed back out/in). Network ACLs, on the other hand, operate at the subnet level and are stateless. They can be used as an additional coarse-grained filter on traffic in and out of subnets. Best practice is to use security groups as your first line of defense (they’re easier to manage per application), and use NACLs sparingly for subnet-level rules or to add an extra layer of network guardrails.
VPC Endpoints

An AWS VPC Endpoint allows you to privately connect your VPC to supported AWS services without requiring an internet gateway, NAT device, or VPN connection. In other words, VPC Endpoints let your instances in a VPC talk to AWS services (like S3, DynamoDB, SQS, etc.) entirely via the AWS internal network, not over the public internet. This improves security and can reduce cost. There are two types of endpoints:
Gateway Endpoints

Currently used for AWS services like S3 and DynamoDB. A gateway endpoint is a target that you add to your route table. It routes traffic for the service (e.g., S3) directly to that service within AWS’s network. Gateway endpoints cost nothing to use – AWS does not charge for using a gateway VPC endpoint. For example, you can set up a gateway endpoint for S3 in your route table; now instances in your VPC can access S3 without going out to the internet, and with no hourly or data processing charges for that endpoint.
Interface Endpoints
These are powered by AWS PrivateLink and are used for many other AWS services (and SaaS/cloud partner services). An interface endpoint creates an elastic network interface (ENI) in your subnet that serves as an entry point to the AWS service. Your traffic to that service is directed to the ENI (staying within the AWS network). Interface endpoints do have a cost – you pay an hourly charge for each endpoint ENI and a per GB data processing fee for traffic through the endpoint . (For example, interface endpoint data transfer is roughly $0.01 per GB for the first 1PB in many regions .) Despite the cost, interface endpoints are often worth using for security, because they eliminate exposure to the public internet and can potentially save NAT gateway data charges (more on this in the pricing section).
Peering Connections and Transit Gateways

These are not components within a single VPC but rather ways to connect multiple VPCs together. We’ll cover AWS VPC Peering and AWS Transit Gateway in detail in a later section, but in brief: a VPC peering connection is a one-to-one networking connection between two VPCs (enabling you to route traffic between them as if they were in the same network) . A Transit Gateway is a hub-and-spoke networking service that can connect hundreds or thousands of VPCs and on-prem networks through a central router. These options matter if your architecture spans multiple VPCs (which is common in larger deployments or multi-account setups).
With these components, you can build complex network architectures in the cloud. Next, let’s look at a real-world example of how these pieces come together in a typical AWS deployment.
AWS VPC Architecture: A Multi-Tier Application Example

Imagine you're deploying a secure and highly available web application on AWS. You'd likely use a Virtual Private Cloud (VPC) designed with both public and private subnets, spanning multiple Availability Zones (AZs) for resilience.
Here's a breakdown of how it works:
- Public Subnets (one per AZ): These subnets host your Application Load Balancer (ALB) and NAT Gateways.
- The ALB has a public IP and acts as the internet-facing entry point, distributing incoming web traffic to your application servers.
- NAT Gateways (one per AZ for redundancy) enable instances in private subnets to initiate outbound connections to the internet (e.g., for software updates) without being directly exposed to it.
- Traffic from the public subnets is routed to an Internet Gateway for full internet connectivity.
- Private Subnets (one per AZ): These subnets contain your sensitive resources, like application servers (EC2 instances) and database servers.
- Instances here do not have public IP addresses, enhancing security.
- They receive client requests forwarded by the ALB and use the NAT Gateway for any necessary outbound internet access.
- Their route tables direct all outgoing internet-bound traffic through the NAT Gateway, ensuring they remain isolated from direct internet access.
- VPC Endpoints (for secure AWS service access): If your application servers need to interact with AWS services like Amazon S3, you can use a Gateway VPC Endpoint.
- This allows traffic to S3 (or DynamoDB) to flow privately within AWS's network, bypassing the NAT Gateway and the public internet. This not only improves security but also eliminates data transfer costs associated with NAT Gateway usage for S3/DynamoDB traffic.
- Security Controls (Layered Defense): Security Groups are crucial for enforcing a "least privilege" network access model.
- For example, application servers in private subnets might only accept inbound traffic from the ALB's security group.
- Database servers would only allow connections from the application servers, creating a robust, layered defense.
This architecture exemplifies a typical three-tier application: a public-facing layer (ALB), an application layer, and potentially a database layer, all built within a secure and highly available VPC.
AWS VPC Peering vs. Transit Gateway – Connecting Multiple VPCs
.png)
As your AWS footprint grows, you may end up with multiple VPCs – for example, one per environment (dev, test, prod) or per application or per department. You might need these VPCs to communicate. AWS offers two primary options to connect VPCs: VPC Peering connections and AWS Transit Gateway. It’s important to understand the difference between AWS Transit Gateway vs. VPC Peering when designing your network architecture.
VPC Peering is a direct networking connection between two VPCs. When you peer VPC A with VPC B, the two act almost as if they are on the same network – instances in A can reach instances in B via private IP addresses, and vice versa, subject to routing rules and security controls. VPC peering uses AWS’s internal, high-bandwidth infrastructure. However, peering is one-to-one: each peering connection links two VPCs. If you have three VPCs and they all need to talk to each other, you would need three separate peering connections in a mesh (A-B, B-C, A-C). This doesn’t scale well beyond a handful of VPCs, as the number of connections grows rapidly and there’s no central management. Also, transitive routing is not supported – if VPC A is peered with B, and B with C, A cannot automatically reach C through B. You would have to peer A-C as well. In summary, VPC peering is best for simple, small-scale network connectivity where only a few VPCs are involved. It has no hourly cost (you pay only basic data transfer charges for traffic that crosses AZ or region boundaries) – for example, data crossing AZs via a peering link is charged at about $0.01/GB in each direction . Within the same AZ, data transfer over peering is typically free (and always free for traffic within the same VPC). Peering also works cross-region, though cross-region data transfer fees apply.
AWS Transit Gateway (TGW) is a managed network transit hub that solves the scaling limitations of peering. Think of Transit Gateway as a cloud router: you can attach (connect) dozens or even thousands of VPCs to a single Transit Gateway, and it will route traffic between any of them. Instead of managing a mesh of peer connections, each VPC just has one connection to the Transit Gateway (the TGW sits in the middle as a hub). Transit Gateway supports transitive routing, meaning VPC A can send data to VPC B via the TGW even if they aren’t directly peered – they just both have attachments to the same Transit Gateway. Transit Gateways are highly scalable and can support up to 5,000 VPC attachments in a region , making them ideal for large, multi-VPC architectures (for example, a hub-and-spoke network for a big organization with many accounts and VPCs). They also allow easy integration with on-premises networks: you can attach VPN connections or AWS Direct Connect gateways to a Transit Gateway, thus linking your VPCs and your on-prem network through one central hub.

The trade-off is that Transit Gateway is a separate managed service and does incur additional costs. You are billed hourly for each attachment (each VPC or VPN connected to the TGW) and per GB of data processed through the Transit Gateway. For example, in one region the cost might be around $0.05 per hour per VPC attachment and $0.02 per GB of data. In contrast, VPC peering has no hourly charge and only nominal data transfer costs. So for two VPCs that just need to exchange a small amount of data, a direct peering could be cheaper. However, for many VPCs or complex topologies, Transit Gateway dramatically simplifies network management despite the extra cost. It’s effectively the enterprise-grade solution for multi-VPC connectivity, with built-in route tables, the ability to isolate groups of VPCs, and even peering between Transit Gateways in different regions for global networks.
In summary: Use VPC peering for straightforward, pairwise VPC connections (especially within the same region and if you only have a few VPCs). Use AWS Transit Gateway when you need to connect multiple VPCs (many-to-many) in a scalable way or want a centralized management point for VPC connectivity (including connecting to on-prem via VPN/Direct Connect). Both can coexist – you might peer a couple of development VPCs directly, but use a Transit Gateway for your production network that has dozens of VPCs. Just remember that neither VPC peering nor TGW by itself allows internet access – these are for private connectivity among networks. Also, security still matters: with both options, you’ll manage route tables and can use security groups/NACLs to control what traffic is allowed between VPCs.
AWS VPC Lattice –Application Networking Feature

No discussion of AWS VPC in 2025 would be complete without mentioning Amazon VPC Lattice, a newer service that extends VPC capabilities to the application layer.
What is AWS VPC Lattice?
In late 2022, AWS introduced VPC Lattice as a fully managed application networking service to help connect, secure, and monitor communications between your services across multiple VPCs and accounts. While VPC peering and Transit Gateway (discussed above) deal with network-layer connectivity, VPC Lattice operates at the application request level. It allows you to define service networks that span VPCs and accounts, and to set policies for traffic management, authentication, and authorization between services.
Think of VPC Lattice as a way to easily achieve service-to-service connectivity in a microservices or multi-account environment, without having to manually configure load balancers, peering connections, or complex routing rules for each communication path. With VPC Lattice, you can register your application services (for example, a set of ECS tasks, EKS pods, or Lambda functions in VPC A and another service in VPC B) with the Lattice service network. Lattice provides a consistent way to route requests between these services, apply traffic policies, do health checks, and even handle things like authZ/authN (it can integrate with IAM for service authorization). Importantly, this works across VPC boundaries and even across AWS accounts, while abstracting the lower-level network complexity.
For beginners, VPC Lattice might be a bit beyond the basics of subnets and route tables – it’s an advanced managed solution intended to simplify inter-service networking as your architecture grows. The key point is that AWS recognizes the challenge in connecting distributed applications, and VPC Lattice is a solution to “make services communicate with each other simply and consistently”. It’s not a replacement for the fundamental VPC components we discussed, but rather a higher-level construct built on top of them. If you are building microservices that need to talk privately across VPCs, or want a unified way to apply networking rules to communications, VPC Lattice is worth looking into. (As of early 2023, VPC Lattice became generally available, and AWS continues to add features to it.)
In summary, AWS VPC Lattice extends the VPC concept to application networking, helping manage traffic between services in a modern cloud application. It’s part of AWS’s evolving toolkit (alongside things like AWS PrivateLink, Service Mesh, etc.) to simplify complex networking scenarios. For most beginners, you don’t need to use Lattice until you reach that level of multi-VPC, multi-service complexity, but it’s good to know it exists as you plan for the future.
AWS VPC Pricing
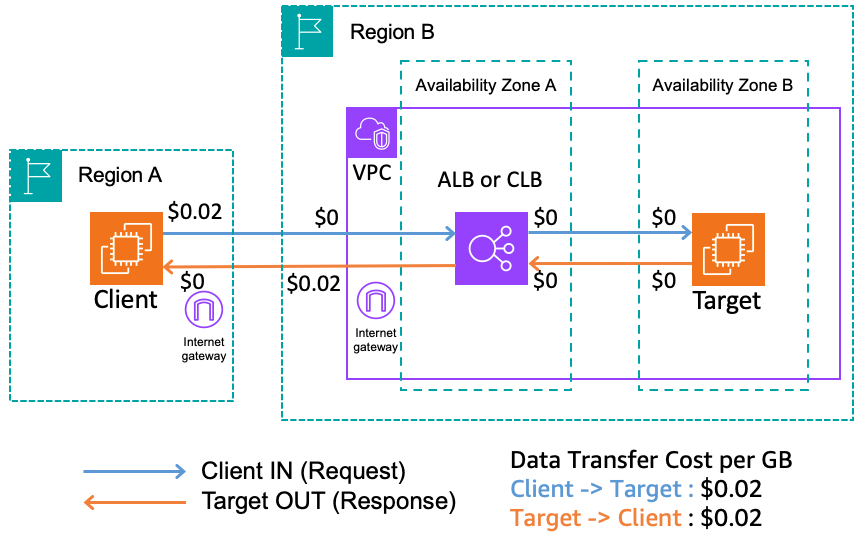
One great thing about Amazon VPC is that the core VPC concept is free – there’s no additional charge for creating and using a VPC itself. You can set up multiple VPCs, subnets, route tables, etc., and these carry no direct cost. However, some VPC components and related services do have costs, and it’s important to understand these to avoid surprises on your AWS bill. Here’s a breakdown of key cost factors in a VPC:
- NAT Gateway Pricing: If you use managed NAT Gateways (as is common for enabling internet access from private subnets), AWS charges for them in two ways: an hourly rate while the NAT Gateway is running, and a per-gigabyte data processing fee for traffic that goes through the NAT gateway . The exact prices vary by region. For example, in US East (Ohio) the NAT gateway costs around $0.045 per hour (which is roughly $32 per month) plus $0.045 per GB of data processed . Data transfer charges may also apply for egress to the internet (standard EC2 data transfer rates). In essence, heavy use of NAT Gateways can become one of the larger VPC-related costs, especially in data-intensive workloads.
- VPC Endpoints Pricing:
- Gateway Endpoints: As mentioned, gateway endpoints for S3 and DynamoDB are provided at no cost – you pay nothing for having or using a gateway endpoint . This is a big incentive to use them for those services, since they can reduce your NAT gateway usage (and thus cost) by keeping S3/Dynamo traffic internal.
- Interface Endpoints (AWS PrivateLink): These endpoints do cost money. You’ll pay an hourly charge for each interface endpoint ENI (usually a few cents per hour, depending on region – roughly $7-$10 per month per endpoint as a baseline), and you’ll pay for data transfer through the endpoint. The data processing fee is on the order of pennies per GB (approximately $0.01/GB for the first petabyte in many regions) . If you have many interface endpoints (for lots of AWS services or AWS Partner services) this can add up. It’s wise to enable interface endpoints selectively for the services that really justify private connectivity. AWS’s PrivateLink pricing page has the full details, and the VPC console will also show a warning that “you are billed for hourly usage and data processing” when you create an interface endpoint .
- Data Transfer Costs: Data transfer charges in AWS deserve a mention. Within a VPC, data transfer is free (for example, between instances in the same AZ using private IPs, or across AZs for many services if using AWS PrivateLink endpoints). However, cross-AZ or cross-region traffic can incur charges. For instance, if you have an EC2 instance in subnet A sending data to another instance in subnet B in a different AZ of the same VPC, AWS may charge for inter-AZ bandwidth (typically around $0.01/GB). Similarly, VPC Peering traffic that goes between AZs is billed at about $0.01/GB (each way) within the same region . Cross-region peering has higher costs per GB. Transit Gateway also has data processing charges (~$0.02/GB, depending on region) on top of any standard transfer fees. Always factor in where your workloads communicate – keeping high-volume traffic within the same AZ or using endpoints can save costs.
- Transit Gateway and VPC Peering Costs: As discussed, VPC peering itself has no hourly fee – you only pay data transfer for cross-AZ/region traffic over the peering connection. AWS Transit Gateway, being a managed service, does have direct charges: you pay per hour for each attached VPC or network connection, and per GB of data processed by the gateway . For example, if you attach 3 VPCs to a Transit Gateway, you’re paying for 3 attachments hourly. In some regions the cost is roughly $0.05 per VPC attachment-hour (so ~ $36 per month per attachment), plus $0.02/GB. Transit Gateway is powerful, but you’ll want to use it where its value (simplified design) justifies the cost. For small-scale setups, simple peering might be more economical.
- IP Addressing Costs: Generally, using private IP addresses in your VPC is free. But note that if you allocate an Elastic IP (EIP) (a static public IPv4 address) and don’t use it (attached to a stopped instance, or not attached at all), AWS may charge a small hourly fee for the idle address. Also, AWS now charges for public IPv4 addresses attached to running resources beyond a certain threshold (AWS provides 750 hours of free public IPv4 usage per month for new accounts under the free tier, but thereafter a modest hourly charge applies for each public IPv4 in use) . This is because IPv4 addresses are a scarce resource. Private IPv4s and all IPv6 addresses have no direct charge.
- IP Address Manager (IPAM): If you need a single place to plan and audit IP space, Amazon VPC IP Address Manager (IPAM) does the heavy lifting. The Free Tier lets you manage BYOIP ranges and Amazon-provided IPv6 for one Region/account at no extra cost. The Advanced Tier unlocks multi-region/account tracking, plus private-IPv4 management and IP-history auditing. Advanced Tier pricing is $0.00027 per active IP address, billed hourly. Only IPs actually attached to an ENI are considered “active,” so unused space isn’t charged
- Traffic Mirroring: Need packet-level visibility for threat-hunting, DPI, or troubleshooting? Enabling Traffic Mirroring on an elastic network interface (ENI) costs $0.015 per ENI-hour. Remember, charges keep ticking until every mirror session tied to that ENI is deleted — even if the instance is stopped or the ENI is detached
- VPC Route Server Endpoints: For BGP-based routing use-cases (e.g., EVPN, SD-WAN overlays) AWS now offers VPC Route Servers. Each Route Server requires two Route Server Endpoints, and each endpoint is billed at $0.75 per hour. Budget for that fixed hourly cost in addition to any data-transfer fees your design incurs.
Summary of VPC costs: The VPC itself is free, but be mindful of the “paid extras”: NAT gateways, Transit Gateways, VPC interface endpoints, and data transfer across AZs or out to the internet. Always consult the official Amazon VPC pricing page for the latest details and regional prices. AWS also provides a cost calculator where you can estimate these costs for your specific architecture. Often, optimizing your architecture (for example, using gateway endpoints or consolidating traffic) can yield significant savings – e.g., the AWS docs note that sending S3 traffic through a gateway endpoint instead of a NAT gateway will avoid NAT data processing charges.
AWS VPC Best Practices
Designing and managing your VPC effectively is vital for security, performance, and cost efficiency. Here are some AWS VPC best practices gained from experience and official AWS guidance:
- Plan Your IP Address Space Early: Choose a VPC CIDR block large enough for your needs but avoid overlapping with other networks you might connect to. For example, if your company uses 10.0.0.0/8 range on-premises, pick a different range (like 172.31.0.0/16) for your VPC to ensure future connectivity. Using unique, non-overlapping IP ranges for each VPC is recommended .
- Use Multiple Availability Zones: Always spread your subnets (and the resources in them) across at least two AZs for high availability . This way, an AZ outage won’t take down your entire application. For instance, create two private subnets (one in AZ-a, one in AZ-b) and two public subnets (AZ-a, AZ-b) and distribute your workloads.
- Separate Public and Private Subnets: Design your network with least exposure. Place frontend or public-facing components in public subnets (only those components should have Internet access). Put databases, application servers, and internal services in private subnets with no direct internet route. This minimizes the attack surface.
- Leverage Security Groups (and NACLs as needed): Use security groups to tightly control traffic to and from your instances . Security group rules should be as restrictive as possible (e.g., allow only specific ports from known sources). Because security groups are stateful and operate at instance level, they make it easier to manage access for each service. Network ACLs can be used to enforce additional subnet-level restrictions or to provide a second layer of defense, but they are stateless and can become complex – use them judiciously (often the default “allow all internal” ACL plus SGs on instances is sufficient for many architectures).
- Use VPC Endpoints to Reduce Dependence on NAT: Where possible, configure VPC endpoints for services like S3, DynamoDB, and others your application needs. This keeps traffic to those services inside the AWS network and avoids NAT gateway data charges . It also improves security (no traffic going out to the public internet). Gateway endpoints cost nothing and should be a no-brainer for S3/Dynamo in private subnets. For other services, weigh the cost of interface endpoints versus NAT usage – often, interface endpoints are worth it for critical or high-volume services.
- Monitor and Log Network Traffic: Enable VPC Flow Logs for your VPC or specific subnets/interfaces. Flow Logs record metadata about traffic (source, destination, ports, allow/deny, bytes transferred, etc.) which is invaluable for troubleshooting and security monitoring . You can send flow logs to CloudWatch or S3 for analysis. They’ll help answer questions like “Is this instance trying to talk to that service?” or “What traffic is being blocked by my security group?”.
- Use Network Analysis Tools: AWS provides tools like Reachability Analyzer and Network Access Analyzer to validate and troubleshoot your network configurations. For example, Reachability Analyzer can tell you if an instance in Subnet A can reach an instance in Subnet B (and if not, which hop is dropping traffic). Network Access Analyzer can scan your VPC for unintended access paths . These tools are great for ensuring your security rules match your intentions.
- Consider AWS Network Firewall for Layer 7 Protection: For more advanced network security, especially in architectures where you need to inspect traffic (filter by IP reputation, block specific protocols, etc.), AWS Network Firewall can be deployed in your VPC. It lets you define firewall rules (stateful/stateless) at the subnet level (usually you’d have a dedicated subnet for the firewall). This is an optional advanced feature – not needed for every VPC, but a best practice in environments with high security requirements .
- Automate VPC Setup with Infrastructure as Code: Treat your network like code. Use tools like AWS CloudFormation or Terraform to define your VPC and its components. The popular Terraform AWS VPC module can create a well-architected VPC (with public/private subnets, NAT gateways, route tables, etc.) with minimal effort, following AWS best practices. Infrastructure as Code ensures that your VPC configuration is reproducible and version-controlled, reducing manual errors.
- Isolate Environments and Use Multiple VPCs if Needed: Don’t shove everything into one VPC if it doesn’t make sense. It’s often a best practice to use separate VPCs for dev/test/prod or for fundamentally different trust boundaries. For example, a public-facing service might live in one VPC and an internal-only service in another, connected only via tightly controlled means (like a Transit Gateway with restrictive route tables or VPC peering with specific security group rules). VPCs are free, so isolation only costs the effort to manage connectivity. This ties into the AWS multi-account strategy as well – often each account has its own VPCs and you use AWS Organizations and Resource Access Manager to share resources or connect networks.
- Regularly Review Your VPC Configurations: Cloud environments evolve. Periodically audit your VPC setup: Are there security group rules open to “0.0.0.0/0” that should be more restricted? Are you using old unneeded peering connections or endpoints? Are there unused Elastic IPs incurring cost? Tools like AWS Config can continuously check for certain misconfigurations (e.g., an overly permissive security group). Keep your VPC tidy and remove unused resources (unused NAT gateways, idle endpoints, etc.) to save money and reduce attack surface.
By following these best practices, you’ll ensure your AWS VPC is secure, efficient, and scalable. A well-designed VPC sets the stage for all the infrastructure and applications you build on AWS, so it’s worth the time to get it right.
Conclusion
For a beginner in AWS, mastering VPC concepts is a major milestone. With this knowledge, you can confidently plan out network architectures for your applications that are secure by design, cost-effective, and ready to scale. As you gain experience, you’ll find yourself leveraging VPC features – from simple things like security groups to advanced capabilities like Transit Gateway and VPC Lattice – to meet your needs. Remember, the official AWS documentation and whitepapers (such as the Amazon VPC User Guide and AWS networking whitepapers) are fantastic resources if you need deeper information on any topic we covered. Networking may seem complex, but with VPC, AWS gives you the tools to manage that complexity in the cloud.
Happy networking in your AWS VPC, and may your cloud networks be ever robust and securely connected!
Monitor Your AWS VPC Spend with Cloudchipr
Setting up your AWS VPC is only the beginning—actively managing cloud spend is vital to maintaining budget control. Cloudchipr offers an intuitive platform that delivers multi‑cloud cost visibility, helping you eliminate waste and optimize resources across AWS, Azure, and GCP.
Key Features of Cloudchipr
Automated Resource Management:
Easily identify and eliminate idle or underused resources with no-code automation workflows. This ensures you minimize unnecessary spending while keeping your cloud environment efficient. For instance, with Cloudchipr, you can detect and delete idle Elastic IPs that often incur unnecessary charges. This ensures you minimize unnecessary spending while keeping your cloud environment efficient.
Receive actionable, data-backed advice on the best instance sizes, storage setups, and compute resources. This enables you to achieve optimal performance without exceeding your budget.
Keep track of your Reserved Instances and Savings Plans to maximize their use.
Monitor real-time usage and performance metrics across AWS, Azure, and GCP. Quickly identify inefficiencies and make proactive adjustments, enhancing your infrastructure.
Take advantage of Cloudchipr’s on-demand, certified DevOps team that eliminates the hiring hassles and off-boarding worries. This service provides accelerated Day 1 setup through infrastructure as code, automated deployment pipelines, and robust monitoring. On Day 2, it ensures continuous operation with 24/7 support, proactive incident management, and tailored solutions to suit your organization’s unique needs. Integrating this service means you get the expertise needed to optimize not only your cloud costs but also your overall operational agility and resilience.
Experience the advantages of integrated multi-cloud management and proactive cost optimization by signing up for a 14-day free trial today, no hidden charges, no commitments.

.png)
.png)
.png)